|
|
Appendix B
Internet explained
History
The idea of interconnecting computers in different geographic locations emerged after WWII. While computers were still in their infancy, the concept existed only in the minds of futurologists and philosophers. The Soviet launch of the 'Sputnik' satellite prompted the US government to invest heavily in technology research and development. The Advanced Research Project Agency (ARPA) was established in the late sixties, and by 1969 four computers had been connected to the ARPANET. In 1972, Robert Kahn held a successful demonstration of the ARPANET to the International Computer Communications Conference and introduced a new application for it – email. The ARPANET network was the grandfather of the Internet as we know and use it today.
In 1977 the ARPANET connected 111 computers, and by 1985 the network had reached Europe and Australia. The Internet was becoming global and de-militarised. 1983 saw the introduction of TCP/IP version 4 – a protocol with which any computer in the world, irrespective of its make or model, could communicate with any other on the same network. This technical breakthrough is regarded as the birth of the Internet. Robert Kahn developed the Transmission Control Protocol/Internet Protocol with four basic principles:
- Network connectivity. Any network could connect to another network.
- Distribution. There would be no central network administration or control.
- Error recovery. Lost packets would be retransmitted.
- Black box design. No internal changes would have to be made to a network to connect it to other networks.
TCP/IPv4 is still the common protocol of the Internet today. Its very structure has so far ensured that no particular person or company runs the Internet, and that all who connect to the Internet are given unrestricted access to its content (we have discussed Internet censorship and filtering earlier).
The World Wide Web
The most popular way of using the Internet today is through the World Wide Web (WWW). The Internet itself is the physical connection of computers with computer networks, whereas the WWW is one specific platform for these computers to communicate upon. The concept and technology of the WWW were developed by Tim Berners Lee and Robert Cailliau at the nuclear physics laboratory Conseil Européen pour la Recherche Nucleaire (CERN) and made public in 1991. The WWW's main features were:
- links – (hyperlinks) that connected one webpage to another
- communication – HTTP (hypertext transfer protocol) - an electronic language spoken by computers on the Internet.
- webpages – HTML (hypertext markup language) used to design webpages and interact with others by means of links.Other popular languages for writing websites in are PHP and JavaScript.
- addresses – URL (universal resource locator) - an addressing system for referencing web pages and other information on the Internet.
Together they constitute the building blocks of the Internet we use today.. The communication between websites is performed by TCP/IP.
Internet Today
According to the Internet Statistics Survey, there were over 1 billion Internet users in January 2006. This is an incredible figure, considering that no one heard of the Internet in 1990. It has become a primary method of information storage and exchange for many people.
A significant recent example of the power of the Internet is Wikipedia.org - an online encyclopaedia, with articles written and edited by the Internet community. Within 5 years since its foundation, Wikipedia.org had over one and a half million articles in English and at least one hundred thousand in ten more languages. Its popularity lead to an independent evaluation of the accuracy of its information as compared to Encyclopaedia Britannica. The results showed that the two encyclopaedias were just about as accurate as each other.123
Basic Infrastructure
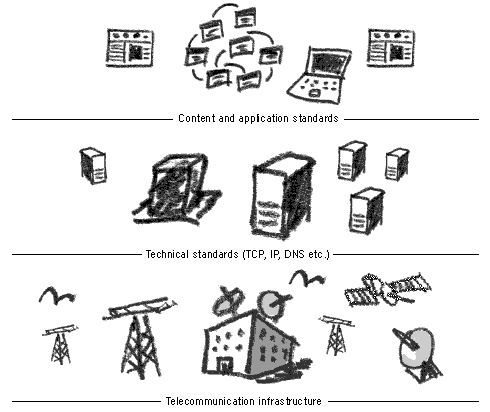
The Internet is the ultimate distributed network. This means that it has no central base or server. Yet, it does apply standards to the way it operates (called protocols) and to the organisations that develop these standards. Today's Internet has 3 main layers to its operation. First, there is the telecommunications infrastructure. A collection of telephone cables, optic fibre, microwaves and satellites - all working together to ensure that Internet traffic reaches the world's every corner. The second layer are technical standards and services. It is composed of different protocols, directing the traffic around the infrastructure and allowing us to view webpages and send email. It is on this layer that we connect to the Internet. The last layer: content and applications - is where all the web pages and Internet services operate. One of the Internet's main strengths is that each of these layers operates independently 124
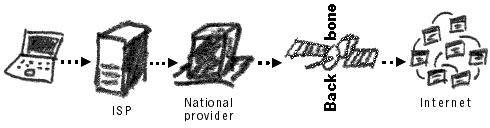
Let's look at how the Internet functions from the end user's point of view. First, we need to be connected to the Internet. This can be done by creating an account with an Internet Service Provider (ISP), which in turn, purchases its own access from a national provider. National providers receive their connection from one of the multinational companies that maintain the Internet's backbone. The backbone is a high-powered and high- bandwidth structure, with global connections via underwater cables and satellites, that enables communications between countries and continents. Also known as Tier1, it is run by companies such as MCI, AT&T, Cable Wireless, and France Telecom.
When you get connected to the Internet, your computer is assigned an IP address. Like a postal address, it uniquely identifies this computer on the Internet. Depending on your Internet Service Provider, you may be assigned different IP addresses at different connection times. All web sites and web servers have an IP address.
www.frontlinedefenders.org is actually 217.67.142.198
However, when we want to visit a website, we don't request to see 217.67.142.198 but type in www.frontlinedefenders.org instead. There exists a method to translate the IP numbers into common languages names. It is called the Domain Name System (DNS), and there are dedicated computers on the Internet whose function is to perform these translations. Therefore, we don't have to burden ourselves with memorising complex number combinations, but only have to remember linguistic descriptions of the website name.
DNS relies on root servers. These are, in plain words, several chosen computers that maintain a list of the most important website names and their relevant identifiers (.COM .ORG .NET .GOV, etc.). Some of these root servers are privately owned and some are operated by US government agencies. The majority of these servers are currently located on the East Coast of the USA. The DNS structure is administered by the Internet Corporation for Assigned Names and Numbers, operating under the jurisdiction of the US Department of Commerce. In effect, some of the major players (those who own and manage the root servers), like Verisign (a B private US company), have the power of veto in this ruling body – the fact that has become a contentious issue for those fearing that the US exerts too much control over the Internet.
To see a web page from your computer, you must request it by typing its website name into the URL. The Internet then finds the website IP by querying the DNS. Eventually, a path from your computer to the destination website must be found. This path could travel through countries, oceans and space; it could be thousands of miles long and could pass through numerous computers. How does it know which way to go, when there exist hundreds of millions of different websites? The task of directing your message to the website (and back) is performed by routers, and the process is known as routing. These routers can be manipulated to record or re-direct their packets or to block access to certain websites.
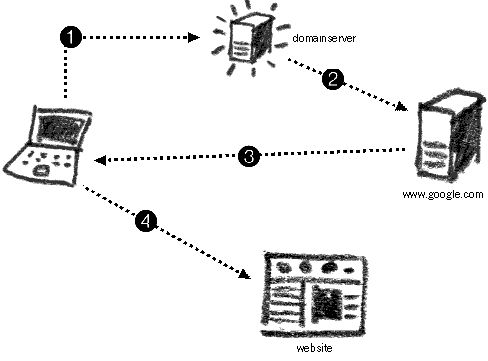
Example of how your message travels on the Internet when finding a webpage through Google
- You type in www.google.com The computer looks to the DNS server to find Google's IP
- The DNS server forwards you to www.google.com
- You type in your search query and are given the results by Google
- You are directed to the result page (note: it is possible that your computer will find the IP of this webpage via the DNS server again)
Every computer or router, which you go through to get to your destination, is called a hop. The number of hops is the number of computers/routers your message comes in contact with along its way. Below, is the path my computer makes on the Internet to get to www.google.com. You can see that my request will pass through at least 13 computers (hops) to get to its destination.
traceroute to www.l.google.com (66.249.93.99), 64 hops max, 40 byte packets
1 217.67.143.157 (217.67.143.157) 74.53 ms 30.910 ms 49.643 ms
2 217.67.140.61 (217.67.140.61) 29.780 ms 28.60 ms 29.628 ms
3 217.67.131.10 (217.67.131.10) 49.987 ms 29.872 ms 29.615 ms
4 217.67.131.6 (217.67.131.6) 40.267 ms 34.815 ms 40.219 ms
5 85.91.0.61 (85.91.0.61) 41.237 ms 39.192 ms 38.831 ms
6 208.50.25.109 (208.50.25.109) 31.452 ms 115.234 ms 37.396 ms
7 so0-0-0-2488M.ar3.LON2.gblx.net (67.17.71.25) 89.496 ms 44.303 ms 46.455 ms
8 ldn-b1-pos2-0.telia.net (213.248.100.1) 47.497 ms 44.190 ms 45.240 ms
9 google-104716-ldn-b1.c.telia.net (213.248.74.194) 52.678 ms 89.984 ms 61.543 ms
10 72.14.238.246 (72.14.238.246) 69.863 ms 72.14.238.242 (72.14.238.242) 59.778 ms 72.14.238.246 (72.14.238.246) 75.364 ms
11 216.239.43.91 (216.239.43.91) 65.671 ms 61.264 ms 53.603 ms
12 72.14.232.141 (72.14.232.141) 55.727 ms 54.204 ms 216.239.43.88 (216.239.43.88) 54.456 ms
13 64.233.175.246 (64.233.175.246) 72.265 ms 53.48 ms 55.586 ms
14 66.249.93.99 (66.249.93.99) 54.490 ms 113.495 ms 66.249.94.46 (66.249.94.46) 57.798 ms
trace complete
If you have used the Internet before, you know that, despite its seemingly complex structure, it is very easy to operate. This simplicity is the result of its stable architecture, as explained above. It allows us to quickly locate what we need in the ocean of electronic information. DNS servers and routers are responsible for coordinating this process. If someone can control or influence their operation, our use of the Internet will be damaged or restricted.
Email
Electronic email is composing electronic messages and sending them around the Internet. Anyone can register an email account on the Internet, or receive one from their ISP, and these hosts will become our email providers. Every email account has a unique address (dmitri@email.com) where the user name is separated from the provider's address by a '@'. Email is sent around the Internet following the same principles of DNS and routing. First, the email provider is found by its domain name (e.g. email.com), then the provider is queried for the existence of a particular user account (e.g. dmitri). If the information is correct, the email is delivered. If not, the email is returned (or bounced) to us with an error message.
Every email message you send or receive contains the following information:
- The name registered for the email account (e.g. dmitri vitaliev)
- The email address
- The IP number of the originating computer or email provider
- The route taken by the email to get to its destination
- The date the email was sent and received
This information is stored in email message headers and usually looks like this:
Received: from hotmail.com (bay17-f12.bay17.hotmail.com [64.4.43.62])
by mail2.frontlinedefenders.org (Postfix) with ESMTP id 5AB164F
for ; Thu, 20 Jan 2005 14:44:06 +0000 (GMT)
Received: from mail pickup service by hotmail.com with Microsoft SMTPSVC;
Thu, 20 Jan 2005 06:44:04 -0800
Received: from 217.67.142.198 by by17fd.bay17.hotmail.msn.com with HTTP;
Thu, 20 Jan 2005 14:43:58 GMT
Message-ID:
From: “Dmitri Vitaliev”
To: dmitri@frontlinedefenders.org
Date: Thu, 20 Jan 2005 15:43:58 +0100
Content-Type: text/plain; format=flowed
X-Originating-IP: [217.67.142.198]
X-Originating-Email: [dmitri@hotmail.com]
X-Sender: dmitrv@hotmail.com
This example shows a message header for the email sent from dmitri@hotmail.com to dmitri@frontlinedefenders.org. You can see the IP of the Hotmail servers (64.4.43.62) and the IP of the computer the email was sent from (217.67.142.198).
All our email and Internet traffic are identified and recorded by the destination/origin IP and the time sent/received. This information is used to authenticate our message and its delivery. At times, it is also used to monitor and restrict our activities on the Internet. The crucial Internet infrastructure, described above, is rather lucrative for surveillance and censorship, simply because security was not on the minds of the original Internet developers.
Websites
A website is a collection of pages written in HTML (and other Internet adaptable languages). A website must reside on a webserver, also referred to as a host. The host provides an IP address for the website, and you must also register a unique DNS name for it, e.g. www.mywebsite.com. One website could share its IP address with many others residing on the same host, yet they will all have unique DNS names.
For stability and security, some websites are mirrored by being copied to different hosts, often in different countries. If your primary website breaks down or is blocked from access, the mirror takes over.
VoIP
Voice over IP is a technical name for "Internet based telecommunications". Instead of using the telephone exchange network, you can have a voice conversation over the Internet. It is an increasingly popular method of communication, because after the initial set-up costs, you are not paying long-distance charges: geographic location is irrelevant to the Internet. Skype is probably the best known program (with around 100 million subscribers) using this technology at the moment125. VoIP has become a major competitor to traditional telecom companies and has faced stiff opposition in the countries trying to maintain the monopoly of telecom- munications.
Blogging
This is perhaps one of the most influential uses for today's Internet. An online diary or an opinion column in its essence, it can be created by anyone on any of the Internet's multiple free blog hosts. You do not need to set up a web- server, nor do you bear any costs. Sometimes, the webpage structure is already custom-built, and all you have to do is fill it up with your content. Blogging provides an opportunity to voice your opinion on any subject of your choice.
In stark contrast to traditional media that expects consumers to simply digest the information presented to them, online publishing is the closest available proximity to a global voice. It is a collection of every article, opinion and blog (currently there are around 50 million blogs) on every existing subject. It carries totally unedited information that only expresses the opinion of its publisher.
'Citizen journalism' is a term, applied to those who report on news, events and changes in their countries through a blog. Often, it is the only source of 'real' news from a country. 'Citizen journalism' has become a powerful weapon in the struggle for freedom of expression, and therefore it is heavily monitored and stifled by oppressive regimes.
Social Networking
This terms refers to the ability presented by the Internet and a variety of new applications for creating and maintaining networks of friends and colleagues. Tools allows you to stay in touch with each other by a variety of methods including instant messaging, photo and video exchange, as well as mobile text messaging. Social networking is responsible for many social causes being brought and promoted on the Internet as well as for relationships between people living in different parts of the world. It has however many inherent dis- advantages and dangers that users need to be aware of. Private information about people is brought online and into the public domain. Relationships between networks of activists are exposed, and can be easily exploited by a determined adversary. Users are willingly sacrificing private information, that is often impossible to remove from the Internet at a later date.
|