|
Digital Security and Privacy for Human Rights Defenders |
1.2 Security awareness
Abstract
This chapter will discuss non-technical approaches to increasing the security of your information and communications. Being aware of your surroundings and thereby realising the potential threats you may be facing is the first step in your security plan. You should also understand your operational environment and have a level-headed approach to the likelihood of security incidents. Securing your operational environmentThe majority of security incidents that affect the work and livelihood of HRDs are connected with physical violence and intrusion into their working environment. Whether you work from an office, carry around a laptop or only use Internet cafés, you should at all times be aware of your capabilities and limitations. Below is a list of questions you should be able to confidently answer. For each question, imagine the worst-case scenario and think how you would deal with it.Office environment
You may note that thoroughness will be required should you wish to secure your working environment and your information. Some of these issues can be easily solved – like purchasing a metal cable to secure your laptop to your desk. Others will require co-operation of the entire staff - like greeting visitors upon entry and querying the purpose of their visit, as well as possible financial investment - like getting insurance or buying a safe. The majority of human rights organisations operate in an open, 'non-secretive' manner, yet they are often responsible for the confidentiality and security of their colleagues and those involved in the cases they deal with (witnesses, victims, claimants, etc.). The ability to look at yourself from a different angle and evaluate your current security situation will go a long way towards forcing you to do something about the insecurities. Assessing the threat to your safety and the safety of your computer must begin at the physical, real- world level. This is an area where you already have experience and expertise. Successful elimination of the risks, posed by the above questions, will provide a very important head start in the security of your digital environment. Consider the diagram on the next page, which displays different layers of security around the information on your computer. Security is all about layers to guarantee in-depth protection through the provision of barriers to access. You must build different layers of protection around important equipment and information. You need to protect access to:
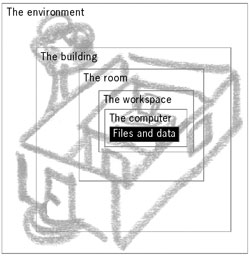
Questions to ask yourselfWhere is my data?First of all, always bear in mind where your most important documents are stored. This could be on the office computer or your laptop or on your USB memory card or even on a pile of CDs in the cupboard somewhere. It is critical that you have a copy of this data (a backup) as accidental loss or malicious damage would put you back several years. It is also important to ensure the security of this backup copy. If your office or home is cluttered with many disks in various locations, then you cannot ensure their safety.Who knows my password?Do not give out your password to anyone, even though you sometimes wish it were otherwise (critical situations, deadlines – we have all experienced this). Work pressure often demands that something be finished first and everything else will be sacrificed for this to happen. From a security perspective, this is a risky practice. Should your password be overheard by an intruder, written down and then lost, or fall victim of an accident, you may lose access to that email account or file forever.
Whose computer is this?Often we need to operate from public computers in an Internet café or a library. Its often impossible to make sure that each computer is free from viruses, spyware, Trojans or other malicious agents. Caution must be applied to the type of information you choose to open on this or that computer. Try to ensure that you do not work with sensitive information that will become a liability if it is corrupted or stolen. Remember that any file opened or read on a public computer can easily be stored for later inspection or abuse if the computer is configured for that.Every computer on the Internet has a unique identifier (more on this later). If the owner of the Internet café records your name and time of visit, then do not think your Internet browsing is anonymous. It could be linked directly to you. Who is this?Whenever a strange email or an unidentified link is received, always ask yourself – who the sender of this information can be. If there are any doubts as to the legitimacy of a message, do not click on it just to find out - delete the message immediately. Unfortunately, the world of computers has come so far that it is not even necessary to double-click on something to get infected with a virus. Modern day techniques can mean that the moment you open an email or a browser you may be infected with the newest brand of some destructive program or other. This is why caution is your best friend.Who can access your computer?When you left your desk for the night or are stepping out for lunch, switch your computer off. Countless incidents can occur while your computer is operating and unattended. By switching the computer off, you are cutting its power supply and securing it from Internet attacks. Your BIOS or Windows security passwords are not effective if your computer is on. Some viruses lie dormant until the middle of the night, then activate your modem and dial a long distance number. It only takes a couple of minutes to boot most computers, so all you are sacrificing is a tiny bit of time while gaining a lot in security. If you are using a public computer in an Internet café or library, try and reset it after you finished working (when using Windows, do this by pressing Start > Shutdown > Restart and wait for the computer to reload). This will clear a lot of the temporary data from your session. Do you know your environment?The knowledge of your surroundings is crucial to your security. You should be aware of the risks and dangers that each scenario presents, and of your resources for dealing with them. Working towards electronic security should include knowledge of relevant local legislation, office workspace security, a trusted circle of friends and colleagues, technical knowledge and awareness of your own and your computer's vulnerabilities and capacities. To prepare a better policy on security for yourself or your organisation, you need to build a threat model. |
