|
Digital Security and Privacy for Human Rights Defenders |
2.5 Internet Surveillance
Abstract
Surveillance and intelligence gathering have moved on – from monitoring phone calls and opening people's mail – to the Internet. Because of the Internet's open infrastructure for seeking and passing content, today's surveillance can be carried out by governments, businesses, hackers and criminals. It is relatively simple to establish mechanisms that will record and monitor all of your Internet activity. All websites log information about their visitors (IP address and time of visit) as do the majority of email providers. Internet Service Providers keep logs of all activity that passed through their servers. Such 'record keeping' has even become mandatory in many countries. In 2006, the EU passed legislation requiring the ISPs to store traffic data of all their subscribers for a period of 2 years,36 although member states can choose to store it for longer periods. Let's have a look at how your Internet activity can be monitored. Monitoring Internet browsing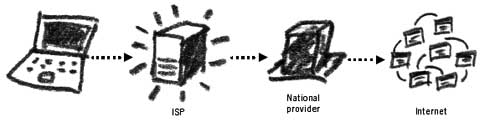
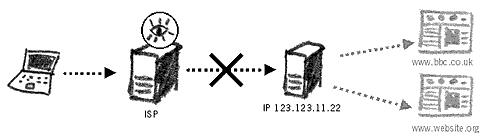
The ISP can monitor your Internet connection In essence, the Internet is just a bigger version of your office network. It's made up of computers, connected by cables, and assisted by servers, routers and modems. Even though your message on the Internet may cross an ocean via an underground cable, bounce off two different satellites and be delivered to someone's mobile phone on a moving train – the system resembles an updated version of the telephone exchange. And when you are an operator, or a wire tapper, or a jealous boyfriend – all you need to do is create an additional receiver on the communicating line and you will hear the entire conversation that goes on. The same with the Internet. Anyone with appropriate access to the network can intercept and read your message on its way around the world. 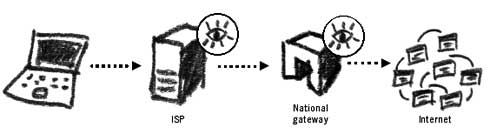
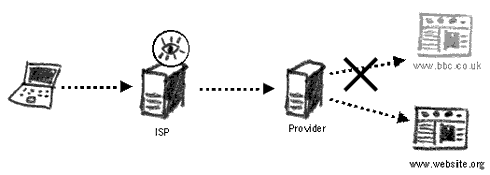
Internet monitoring at the ISP and the national gateway In the late Eighties, the US, UK, Canada, Australia and New Zealand began to develop a global surveillance system that would encapsulate all major traffic points on the Internet. The events of September 11 in the United States led to huge investments to improve the system known as ECHELON which oper- ates under the supervision of the National Security Agency (NSA). It is not known for how long ECHELON keeps the traffic data. It may seem that on a global level it is difficult to efficiently analyse and categorise all Internet and telephone communication in real-time, but the NSA claims a 90% success in doing that.40 Monitoring Website ActivitiesRecords of our Internet activity are further stored on websites we visit and on our personal computers. Many websites require the installation of a cookie on our computer. A cookie is a small amount of data that stores specific user information. For instance, it could record our country of residence, so that we are presented with a relevant country page when visiting a particular website. This is often practised by airline websites, for example. Other information could include the links we have followed to arrive at this or that website, or even personal data from our own computers. After browsing the Internet for a month or so, you may have hundreds of different cookies on your computer. Accessing them can reveal information about your interests and affiliations. A cookie on your computer can act as proof of your visiting a particular website. The largest Internet advertising service, DoubleClick, has agreements with thousands of websites and maintains cookies on over 100 million users, each linking to hundreds of details of the user's browsing habits.41 It is possible to delete cookies from your computer. This can be done from your Internet browser or by finding and deleting them manually. It is also pos- sible to tell your browser not to accept cookies at all. This may result in many websites refusing to open on your computer, but will provide you with maximum protection from cookie infiltration. Use the Ccleaner tool in the Security-in-a-Box project to delete cookies from your computer42. Monitoring EmailEmail communication works on similar principles as website browsing, except that each message has an individual (or a group of people) as its destination, also connecting to the Internet through their ISP.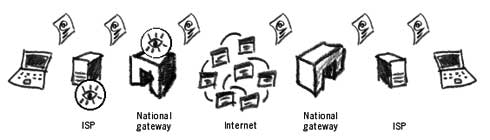
Monitoring email at the ISP and national gateway Hence, an email message will pass through your ISP, the national gateway of your country, around the Internet proper, and then arrive at the national gateway of the receiver, followed by their ISP, before finally being read. Following this schematic, our email message can be intercepted at all major routing points on its way. If you live in a country with strong legal protection of privacy, its legislation won't apply when your email reaches the ISP of the recipient in a country with different privacy and surveillance laws. Bear in mind that whilst your email is on its way from country A to country B, it could pass the routers of several other countries (and companies) on its way. Many ISPs and email providers keep a copy of all emails on their servers. Sometimes this is to our benefit, as we may want to access an email that was sent to us 3 years ago. However, it also allows an outside party to request/demand access to our email accounts. Yahoo! has previously handed over to the Chinese government account information of four Chinese democ- racy activists and scholars resulting in their arrest and conviction.43 Website Filtering & CensorshipApart from monitoring Internet traffic, government and telecommunications companies have the ability to prevent access to certain websites or control the output of results from a search engine query. Filtering access to information on the Internet is in essence a form of censorship and in breach of Articles 18, 19 & 20 in the Universal Declaration of Human Rights (UDHR44) that declare that every person should have the right to freedom of thought, religion, opinion, expression and association, as well as to "..seek, receive and impart information and ideas through any media and regardless of frontiers.'' Internet CensorshipNumerous countries ban access to certain websites for their citizens. Often these websites carry information on extreme religious viewpoints and propaganda, support and help spread terrorist sentiment, or exist to display and distribute pornographic images of children. Some countries choose to block access to websites that criticise or expose government policy, discuss issues of human rights or provide tools that could enable one to bypass their censorship technology. The OpenNet initiative studies trends and technology of Internet censorship and content filtering around the world45. 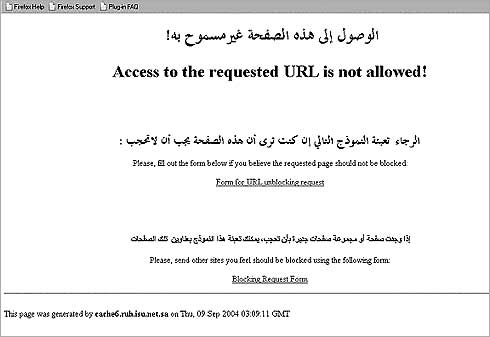
A screenshot of a blocked website from inside Saudi Arabia Websites can be blocked from access using one of three common methods: IP address blocking, tampering with copies of the domain name system, and blocking of URLs. In simple terms this means that a website can be blocked according to its Internet address, name, or the system that translates their name into an Internet address. Blacklists & DNS TamperingNote: a basic understanding of how the Internet functions is required before reading the following sections. Please refer to 'Appendix B – Internet explained' Although they vary in costs and point of installation, all website censorship systems operate on a similar principle. Requests made by the user for a par- ticular website are checked against a list of banned URLs. If the match is pos- itive, the request is denied. Similarly, blacklists may contain IP addresses of servers and deny requests to that address.
Blocking an IP from access
This method will block a website's IP number from being accessible. A problem arises however, when blocking websites by IP. Sometimes these websites sit on large web servers that host several thousands of different websites. These web servers only have one IP. Blocking a website's IP address effectively blocks all other websites sitting on the same webserver.47
Blocking the BBC website by its URL
In the example above, the filtering exists to block all requests made to www.bbc.co.uk. Should the website be re-registered or mirrored under a different domain name, it may become accessible again. These rules can be applied separately or together to create filtering and blocking capacity. Some countries rely on the pre-defined categories of the filtering software and add new websites to its configuration, whilst others employ huge teams of people to scan the Internet and catalogue what should appear in the filter. DNS hijackingThis method refers to directing a user's request to an alternate website. When you enter an address of a website you wish to visit, you are automatically redirected to another website. Some users may not even notice the difference.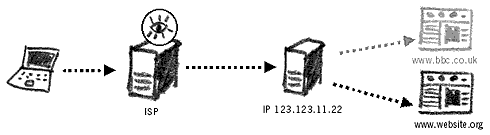
This censorship technique may be circumvented, however, by users specifying one of the root servers as their DNS point of reference, rather than to the local copies stored by their ISPs48 
A screenshot of the Chinese Internet hijacking the www.google.com DNS On September 8th 2002, users in China were prevented from going to Google's web search page. Instead, they were re-directed to a number of China-based pages. The address in the URL said www.google.com49
Keyword FilteringA relatively new method of censorship but one that is gaining strength and widespread implementation is keyword filtering. This involves the banning of certain words or phrases, either in a URL or a page's content. The system allows for broader ability to censor websites and Internet communication by content, as well as enabling the blocking of a particular page within a website and not the entire site itself. However, keyword filtering can be crude, and is likely to prevent access to innocuous as well as intended target sites. The same methodology is applied to search engines and instant messaging tools like Yahoo chat and Skype. When you enter a search query into Google, it is passed through the ISP and a country gateway, before you get a reply. A filtering system could intercept your search for 'human rights' and return a null or wrong result. Below are images of a search result from 2004 on 'falundafa' (a banned spiritual movement in China) performed on Google.com from China.
36
37
38
39 40
41
42
43
44
45
46
47
48
49 50 |