1.3 Threat Assessment & the Security Circle
Abstract
- Write a list of possible threats to the security of your information.
- Try to foresee and take necessary measures to prevent security threats from being realised.
- React to incidents swiftly and investigate the causes.
- When reacting to a security incident, assume the worst possible scenario and take relevant measures.
- Approach security from an all-round perspective. Eliminate the weak links in your strategy and do not compromise the people who you work or communicate with by being careless about security
- Lay out your findings in a diagram. This will allow you and your colleagues to grasp the big picture more quickly.
- Concentrate on the weakest point in your security strategy
To decide what security precautions to take, you need to have a fair idea of the threats you face. These include threats to the security of self, staff, reputation, information and financial stability. All these factors can be compromised in one way or another by electronic insecurity. Since everyone's situation is different, only broad examples are provided to highlight the general idea of modelling the threat.
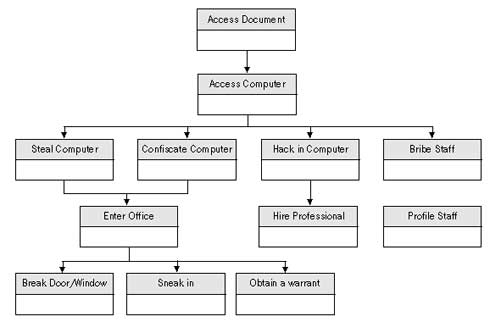
The diagram is written from top to bottom. At the top level, we describe what it is we want to protect. The threat is the ability to compromise this. As you go down one level, you are listing the different insecurities that can occur – the threats to the protection of the upper level. The first example models the threat of someone accessing a document on your computer.
At the top level, write the threat that you want to prevent. In this
case, to access the document, one will need to have access to the
computer first. Access to the computer can be obtained by theft,
confiscation, hacking or bribing one of your colleagues, and so on. You
can choose how many levels down you want to take the model, depending on
what is useful.
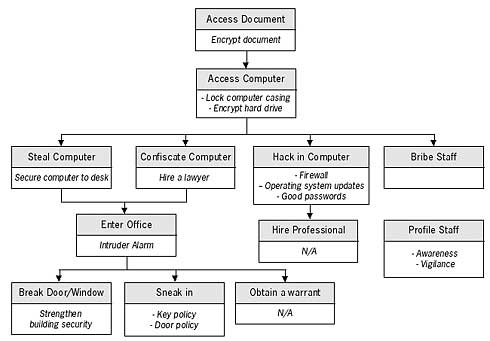
Now, working from down up, fill in the empty parts of the threat boxes with something that will remove or reduce the particular threat. Some of the threats you may not be able to change (like the police obtaining a warrant to enter your premises) but the majority of them you can influence. Work upwards until you have reached the top again.
At this point, you can make a decision as to which of the threats you are willing and capable of defending yourself against. Perhaps you can develop and introduce certain policies and safeguards within your organisation to further reduce the level of threat. You can study methods in this manual on how to protect yourself from hacking and spend some money on securing the entrance points to your office.
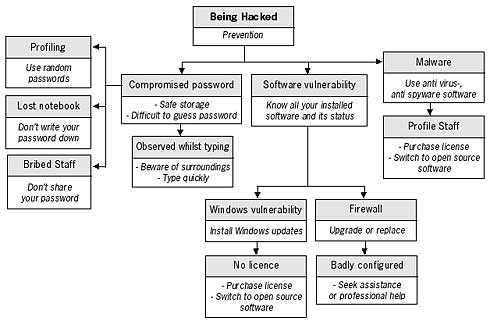
You can continue to develop your model by adding a cost or a time dependency limit to each box in the tree. Upper boxes will have the totals of all boxes beneath them. Such methods can help you with deciding budgets or resources to allocate for preventing a possible threat from occurring.
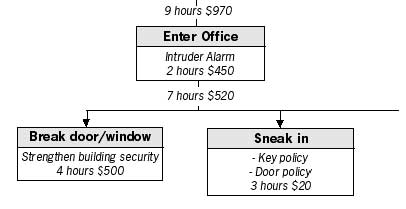
You can also evaluate individual threats from the diagram above. For example, to assess the threat of your computer being hacked (an outsider gaining electronic access to your computer) use the diagram below. At first, it is perhaps difficult to realise all the threats you may be facing, especially in the digital domain. The knowledge will come with further research into the specific areas of electronic security. After studying this manual, your understanding of some technology-related threats should increase. It will then be advisable to detect the sensitive areas of your work and assess the threats you face. Although this may seem like mapping out rational decisions one would take anyway, the process can help you realise and deal with numerous factors that contribute to your insecurity, and prevent accidental mistakes.
Prevention
As opposed to threats encountered in the physical world, digital threats are sometimes difficult to notice and hence to prevent. The tendency is to be reactive rather than proactive with electronic attacks: the latter, more often than not, proves ineffective. A firewall must be installed before you are hacked, a virus cleaner must be updated before you lose documents due to a new virus infection. To deal properly with the possibility of a digital attack, one has to be extremely vigilant and paranoid. The threat model needs to be assumed at the very beginning. The worst case scenario must be understood and dealt with before it happens. The speed of computer and Internet operations means that security barriers are bypassed in a split second. Microsoft is of the opinion that 70% of Windows users do not have any anti-virus or anti-spyware software installed7. The reason for this is not the cost – there are several free anti-virus, spyware and firewall tools – but complacency8. Don't wait until tomorrow to update your operating system, don't wait until you get a virus warning to update your anti-virus software, don't wait until your computer is confiscated or damaged before running the necessary tools to delete or back-up your data. Be proactive!
Reaction
If your computer, password or network security has been compromised, you must assume the worst and take the necessary measures. If a virus has been found on your computer, disconnect it from the Internet. Run a full scan of your entire system and quarantine any virus that has been found. When you no longer get any warning messages, re-connect to the Internet and update your anti-virus definitions and Windows operating system files and do a search for the virus name to see what is known about it on the Internet. You could find information about the damage the virus causes and how to eradicate it properly from your system. Here's a guide to some common examples of computer malfunctions and suggested reactions to them. Digital Security Toolkit
| Incident | Primary reaction | Method | Follow up |
|
Virus attack |
- disconnect from the Internet & run full system scan
- update all virus definitions and operating system
- run full system scan again
|
- run ‘boot scan’ on Avast anti-virus or full scan with AntiVir
- update Avast (or AntiVir)
- run another boot scan with Avast or full scan with AntiVir
|
- research virus on the Internet
- retrace to the moment of infection
- scan all backup and removable devices
- recover virus-affected settings
|
| Spyware attack |
- disconnect from the Internet & run full system scan
- update anti-spyware definitions
|
- run full system scan with Spybot
- update Spybot
- immunise computer against new spyware definitions
|
- research spyware on Internet
- change all system and Internet passwords
- change to using Firefox or Opera browser (if using Internet Explorer before)
|
| Document corruption |
- recover document from backup
- search the temporary folders for recently modified documents (see ‘Windows security’ chapter)
|
- browse through your previously made ‘Freebyte’ or ‘Abakt’ archive
- see chapter on ‘Windows Security ‘ for tips on searching your computer
- use ‘Handy Recovery’ program to analyse the computer
|
- find the cause of computer, document crash
- update computer settings
- update backup and backup procedure
|
| Slow computer operation |
- verify you have enough space on hard drive
- uninstall unnecessary or recently installed programs
- In Windows (NT,2000, Me, XP), check the ‘event viewer’ to see list of symptoms11
- Check for viruses, spyware
|
- use ‘BCWipe’ to delete temporary files on computer
- use ‘Registry FirstAid’ to scan and clean the Windows registry
|
- Disable Windows services (see Johansson’s guide12)
- Purchase more RAM
- Call in a technician
|
| Your access to a website is blocked |
- Find out if others can access the website, ask friends from a different country
|
- see appendix B ‘Internet explained’ & ‘Circumvention of Internet censorship and filtering’ chapter
- install ‘Mozilla Firefox’ and ‘switchproxy’
- install ‘Tor’ or run ‘Torpark’
|
- use a proxy server or anonymity network
- use a translation website that can fetch the website content
|
| Your website is blocked |
- Call the Internet provider to query the blockage
- Move your website to a different host or domain name
|
- see appendix B ‘Internet explained’ & ‘Circumvention of Internet censorship and filtering’ chapter
- use ‘Httrack’ (OpenCD) or ‘SmartFTP’ to mirror your website on a different server
|
- inform network of contacts about site block
- Host website on several computers by mirroring. Ask friends and contacts to mirror your website
- Query the reasons for blocking your website and develop strategy of appeal or compliance
|
| Email does not arrive to recipient |
- send email from a different account to recipient (also webmail)
- do a trace route to recipient’s domain. (see ‘Internet Explained’ appendix)
- verify the email address is correct
|
- see appendix B ‘Internet explained’
- see Encryption on Internet section in ‘Cryptology’ chapter
- use ‘Soft Perfect Network Scanner’
- use ‘Hushmail’
|
- clean your computer of malware and install, update firewall.
- begin using different email accounts (that offer higher security)
- communicate over a different medium (online chat, website forum, telephone
|
| Warning of a raid |
- do a threat assessment
- protect sensitive information
- wipe sensitive information
- make backup of information
|
- Review security policies
- use ‘Eraser’ to wipe data
- use ‘Truecrypt’ and ‘Freebyte’ to backup data to a secure location
- use ‘DeepBurner’ to backup to CD or DVD disks
|
- introduce security policy in office
- strengthen office security
- ensure a safe backup off-site
- develop system for quickly destroying data on computer
|
| Receiving unwanted email (e.g. SPAM) |
- install spam filter or switch to using Thunderbird with built-in filter
- block email addresses
- run virus and spyware scan
|
- use ‘Mozilla Thunderbird’ and read NGO in a Box SE chapter on setting the junk mail filter
- use ‘Avast’ or ‘AntiVir’ and ‘Spybot’
|
- change email address
- develop a vigilant policy on publishing information with your email address
- register additional email addresses that you use to sign up to services on the Internet
|
Description of the ‘security circle’ – all round security
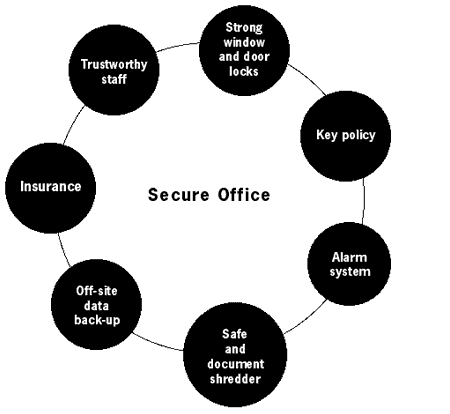
Your security is only as strong as its weakest point. There is not much sense in buying a strong metal door for your office, if you have no idea of how many copies of keys there exist to it. Your court case defending a victim of a human rights violation may not be successful, if your facts are not correct. You must always evaluate the entire scope of your security situation and be ready to notice and deal with all weak points, as it is often those that undermine the whole security process. This also applies to electronic security. Spending money on an expensive firewall will not prevent your computer from physical damage or theft. Implementing an encrypted mail system will not have much effect on your project's communication strategy, if other members of the project do not implement the same. We must approach our security from the perspective of a closed circle. All elements must support each other and weak links must be treated with the utmost care11. Let's have a look at the process of establishing a secure office.
You can probably imagine how a lapse in one area of this circle can lead to a collapse of the entire system. It can of course be slightly more complicated: the alarm system and safe will have a secret combination to open or disarm them. Whoever knows this combination will be able to compromise this system. The 'trustworthy staff' component can, unfortunately, also be a misnomer at times.
A little security is still better then no security at all. Do not be daunted by the difficult scenarios described in this chapter. Be a little paranoid and take extra care in your computer operations. Learn more about the technology you are using and the relevant legislation in your country. It is better to have a long password that a short one, to use encryption than not to use it. But do not rely too much on electronic security without becoming aware of all the complexities first.
|