|
Digital Security and Privacy for Human Rights Defenders |
2.7 Encryption on the Internet
Abstract
Encryption has become one of the last resorts of privacy on the Internet. It enables us to make our messages and communications unreadable to all but the intended party. A layer of encryption was even built into the Internet infrastructure to allow for secure financial transactions. It is called the Secure Sockets Layer and is often abbreviated to SSL. At its inception it was met with strong opposition from the US government. At first, branches of the government tried to ban all SSL encryption of the complexity higher than they could decrypt, or to outlaw its use altogether. Eventually this policy was overturned thanks to a collective effort from mathematicians and activists in a period that become known as the 'Crypto Wars'. Today, SSL is widely used all throughout the Internet. The advantage of using SSL in webmail services is that the technology is already built into the frame- work of the Internet, and national legislations restricting the use of encryption cannot be practically applied. If a nation allows the Internet within its borders, it accepts that SSL exists and is used throughout Internet operations. Organisations can (and often do) offer internal webmail services protected by SSL. It is the minimum requirement today for a degree of privacy of email and Internet communication. The existence and functionality of an SSL connection to a particular website can be identified by two distinguishing features: 
SSL CertificatesThe SSL system works on the Public Key Infrastructure (PKI) concept. All websites wishing to use SSL encryption must obtain an SSL certificate. Your Internet browser communicates with the webserver and encrypts all information sent between the two points. The strength of the encryption depends on the SSL certificate at the webserver end. The Internet standard at the moment is 128/256 bits, which is strong enough for nearly all instances.Your Internet browser (we assume it is Internet Explorer or Mozilla Firefox) has a built-in list of trusted SSL Certification Authorities. If you browse to a website that presents you with an SSL certificate, your browser will automatically check whether it was issued by a trusted authority on your list and whether all its details are correct (i.e. they do not arouse suspicion). Each certificate contains at least the following:
If the authority that issued the certificate is not on your list, or one of the certificate's details could be a cause for security concern, your browser will issue a warning and will allow you to examine the certificate. 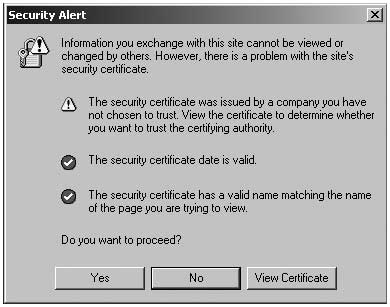
Internet Explorer Certificate Warning 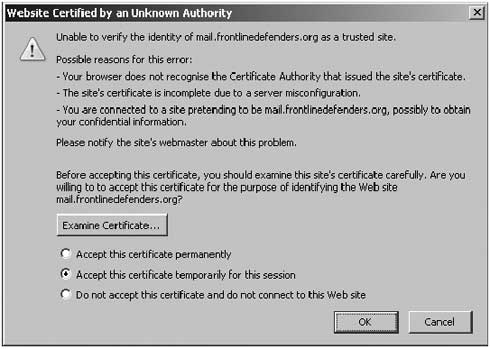
Mozilla Firefox Certificate Warning Note: This does not happen automatically if you are using Internet Explorer, in which case you first need to set this option in the program. Select: Tools > Internet Options 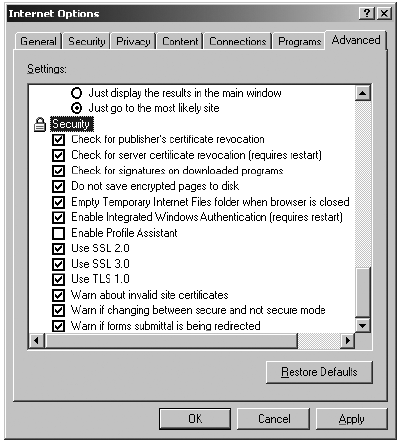
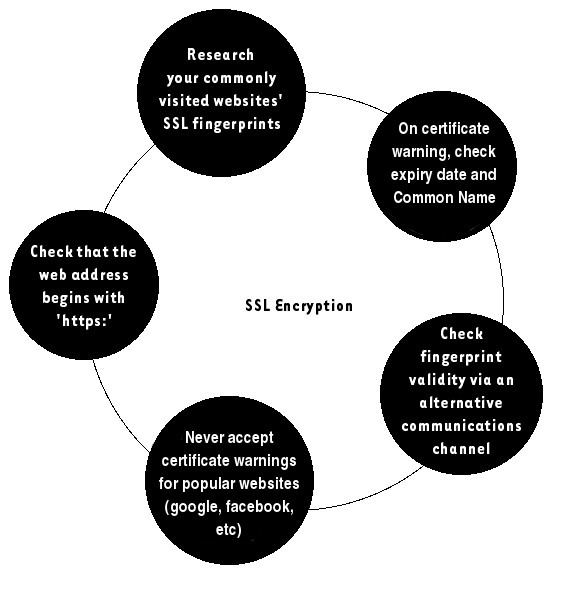
Advanced Internet settings of Internet Explorer Both of warning messages refer to the same problem, although they look different in their respective programs. In both cases you have the option of examining the certificate yourself and then deciding whether you wish to accept it or not. If you do not accept it, you will not have access to the website. If you do choose to accept it ('Accept this certificate permanently' in Mozilla Firefox), then the certificate and its issuing authority will be added to your trusted list and you will not be asked for approval of this certificate again! Note: Different versions of the two browsers may present a slightly modified message, although the main principles and options will remain the same. If you need to inspect the certificate, you should be aware of the things to look out for. The main identification feature of the certificate is its fingerprint (sometimes called thumbprint or MD5). It is the verification of this fingerprint that can positively identify the certificate has really been created and issued by the owners of the website you are visiting. To validate its authenticity, you will need to contact the website owner and check the fingerprint with them manually (by phone, fax, Internet chat or in person). Although this may sound quite annoying, it is a necessity of good security, and the next section will explain the vulnerability you expose yourself to if you do not follow this procedure. If the fingerprint does not match, do NOT accept the connection. You will not be able to access that website from the same Internet connection, however you will prevent being a victim of a Man-in-the-Middle attack (see below). 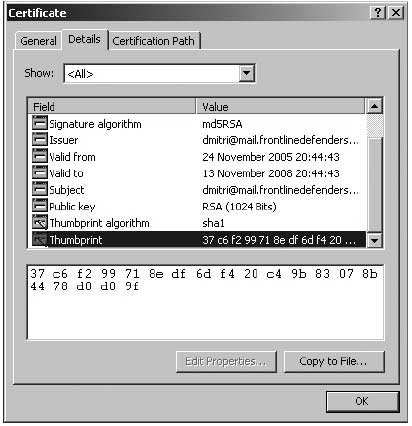
Internet Explorer Certificate Information 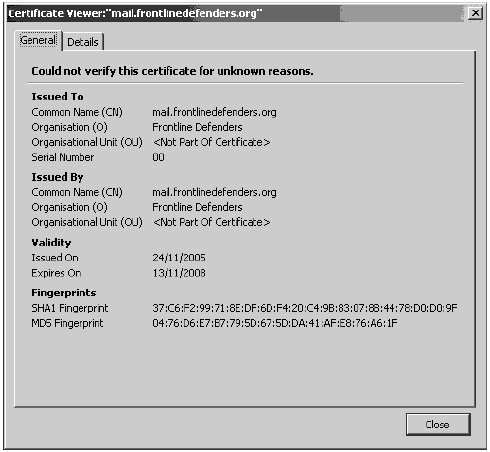
Mozilla Firefox Certificate Information Secure EmailSSL connections have been built into email services on the Internet. This applies to webmail as well as to hosted email. Some webmail accounts offering such security measures free of charge are:(an option in 'Settings' can force an SSL connection) These webmail services allow you to enter your email account and communicate with it on an encrypted connection. Even though this data can still be captured by any filtering or surveillance mechanism, it will be next to impossible to make sense of it or decrypt it. Notice how the addresses are deliber- ately written with 'https:' in the beginning. 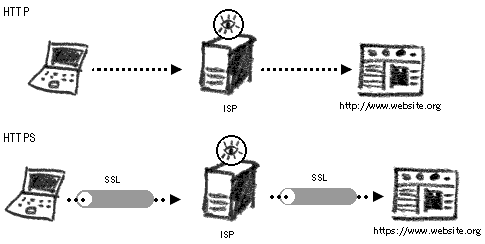
Security CirclePlease note that the recipients of your email may not be using similar security when connecting to their webmail account. As soon as your email hits the recipient's webmail it becomes prone to the security standards of his/her server. If the recipient connects to his/her webmail using an open (non-encrypted channel), surveillance agents at the ISP or a national gateway will be able to scan and read your message in full.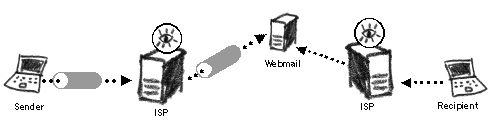
Encrypting one side of the communications channel The security of this approach can further be improved if both parties use the same SSL webmail service provider (RiseUP, Bluebottle). Email, travelling on the Internet between servers, is usually unencrypted and can easily be intercepted. 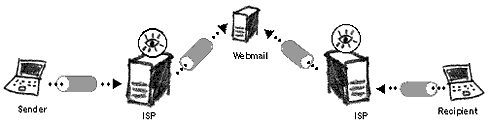
All-round SSL encryption in email communications There is a security consideration when both parties use the same SSL web-mail service. It is the webmail server itself that stores and processes all your messages. Even though your connection to the server is encrypted, the email is accessible to those who maintain the server or hack into it. You may wish to research the security and reliability of your webmail provider as well as the country where it is located. This becomes an issue when you consider a country like the United States, where authorities can issue a subpoena to confiscate the server and all information on it. The above-mentioned webmail servers are situated in the following locations:
The ability to protect your information from the provider has been offered by a number of webmail services. The latter not only use a secure channel of access but also encrypt your data on the server. Your webmail account can only be accessed and opened by you. Email sent to the recipients, who have an account with the same provider, can also be encrypted. Such webmail providers offer a higher level of communication security, but usually require a relatively fast internet connection, for every time you access your account, the website automatically installs temporary encryption software on your computer.60 Services, allowing you to register free accounts, are: Man-in-the-Middle (For Techies)The biggest threat to the SSL Certificate model is what is known as a Man-in-the-Middle (MITM) attack. At its most basic, it is an interception of your Internet information stream – your communication with a web server. It can be used specifically to break the otherwise secure SSL model explained above. First of all, the adversary must get physical access to your Internet line. This can be done at the ISP, a national gateway or even a local network. The adversary then tricks you by presenting an alternative certificate when you try and access your secure webmail account. Only this certificate is not from the web-mail provider, but belongs to the adversary. By accepting the certificate, you enter into a connection with your website through the adversary's server. As you input your information – login details, financial details, witness testimonies – the adversary receives it all without an effort.The problem is that it is very easy to get you accept a certificate you have yourself presented. People tend to click 'OK' without reading the messages. An adversary might be motivated to carry out a MITM attack when they cannot read your email and other Internet transactions because you are operating over 'HTTPs'. They can see you accessing your webmail server, but cannot see the email you read and write. When your Internet line has been intercepted and you accept the adversary's certificate, all your data transmissions during this (and, possibly, future) sessions will go via the adversary's server. This means all your login details, private email, etc. Another problem is that once you have been successfully attacked, it is very difficult to notice that your connection is being routed through another computer. 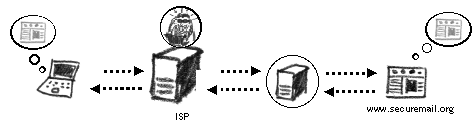
Man-in-the-middle. Your communication channel is intercepted and relayed by an adversary. Whenever your Internet browser asks you to verify the SSL Certificate, ask yourself two questions:
If the answer to question 1 is 'no', then you either did not save the certificate permanently or are facing a Man-in-the-Middle attack. As mentioned earlier, your browser will not ask for your acceptance of a certificate you have previously saved. If you are being asked a second time to accept a certificate to a website whose details should already be in your trusted list, it is probably not the same website.
Note: If you are in an Internet café, you may not be able to verify whether the fingerprint has already been accepted. It is advisable to write down your website's fingerprint the first time you access it from a secure location and then verify it every time you access it from other locations.
Answer question 2 by inspecting the certificate's fingerprint and contacting the website owners (best done by telephone or secure email) to verify it. This may take some time and could be frustrating. Unfortunately, such is the structure of the SSL Certificate system on the Internet and the only option we currently have. There are not that many websites using SSL technology. They include some webmail providers, online shopping and other online financial services. You may only ever be accessing 2 or 3 such websites. Prepare yourself by writing or phoning the operators of these websites and recording their SSL fingerprints. Thus you will be certain of its authenticity when having to review and accept an SSL certificate from their service. If the adversary manages to successfully trick you, they will receive all the information you've input into the website. If it is an email account they have managed to intercept, the adversary will get your login details, and will be able to login to the webmail account themself - a common attack that has claimed many victims on the Internet. It is therefore very important that you understand the procedure of SSL certification and know how to protect yourself.
60 |