|
Digital Security and Privacy for Human Rights Defenders |
2.1 Windows Security
Abstract
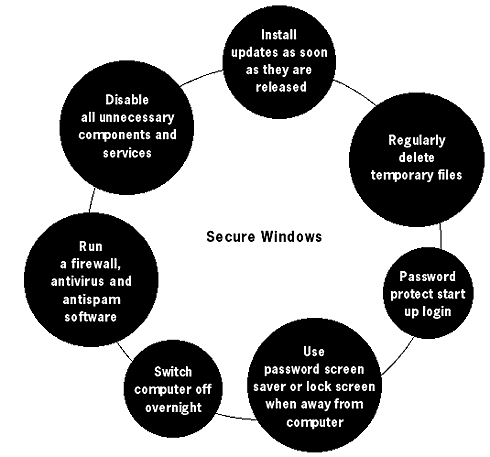
We have discussed the security of your working environment and the importance of awareness of your computer operations. This chapter introduces a more technical aspect. The stability of your computer's operating system is integral to its operation. Different software and hardware could have a negative impact on its functionality and security, if you do not possess the ability to monitor and control it. Your operating system gives you the opportunity to increase (or decrease) the security of your computer by adjusting various settings. It is like your computer headquarters. Whilst security does not depend solely on the operating system, it is important to know the vulnerabilities and the critical administration points of your operating system. The Windows operating system (OS) is well-known for its many security vulnerabilities, but if you do not change to a different OS (e.g. the Ubuntu distribution of the Linux operatung system12), you should at least be aware of the best methodology for securing what you have. This section is divided into different categories and sorted by versions of the Windows OS. It is worth noting that specific versions of Windows, like XP Professional have numerous security features, yet they are not switched on by default. You have to activate them yourself. UpdatesWindows updates are additions to the OS which were not included in the initial release. They are usually upgrades and patches to resolve discovered vulnerabilities. The large releases are called service packs. Microsoft has stopped releasing these updates for Windows 95, 98 and NT. You can find and download all the updates from the previous years, but you will not receive the continuous support. The Security updates and fixes for Windows 2000 and XP will be available at least until 2011.13If you do not have Internet access, you are less vulnerable to many of the electronic attacks. It is still advisable that you find upgrades for your OS on disk or CD. You can always write or email to Microsoft and request the latest service pack (bear in mind that you will need to include licence details of your original product). If you are connected to the Internet, you can visit http://update.microsoft.com and follow the process on the website to discover your current Windows version and updates, and to install all the necessary ones. If you are running Windows XP on your computer, then the website will first check that your Windows software licence is valid. Even if your Internet connection is slow and expensive, I would strongly advise you to install these updates. If Internet connectivity is an issue, I suggest you install just the 'Critical Updates'. You can also obtain all updates for any operating system by going to the Microsoft Catalogue website14 and downloading the required files. This is a useful option to share Windows updates amongst many computers, without having to connect everyone to the Internet. The Microsoft Catalogue has updates for all versions of its operating system and does not check the licence validity of your product. Users of Windows ME, 2000 & XP, who have a constant connection to the Internet, can specify Windows to periodically check for updates and install them upon their release. Go to the Control Panel and select (in 2000 - Automatic Updates, in XP – Security Centre). Choose the options that will automatically download and install the updates.
Lock ScreensEvery Windows computer gives you an option to password-protect imme- diate access once the computer has powered on. This could either be a lock screen, or a password-protected screen saver. Lock Screen – Windows NT, 2000 Lock Screen – Windows XP Screen Saver – (all Windows versions) Go to: Start > Search (for files & folders) The results will show up all the screensavers on your computer. Choose any screensaver and right-click on them. For Techies
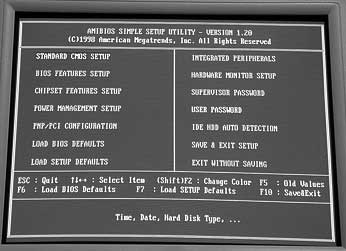
Every computer has a BIOS – Basic Input/Output System. Its purpose is to give your computer initial instructions to begin with. BIOS is a set of essential software routines that execute when you switch on the computer's power. They test the hardware devices, start the hard drive and operating system. The BIOS instructions are stored in a place called ROM – Read Only Memory, and are usually invisible to the user. However, most computers give you the option to inspect and configure the BIOS settings. These include password protection. To enter the computer's BIOS, you are usually requested to press a certain key on your keyboard at the initial power-on screen. This is often the F1 or F2 or F10 or F12 key, depending on the type of BIOS you have. Sometimes, this can also be the ESC or DEL key. Some computers skip through this screen very quickly and you may have to press the 'Pause' button on your keyboard to read it properly. We will only discuss the password settings here. Do not change other standard BIOS settings, if you do not know their purpose. Not all BIOS are the same, but you will find either two or all of these passwords in yours. Power On password – This will protect the BIOS from starting without a valid password. No devices will be loaded, and your computer will not start.
Setting these passwords will prevent immediate access to your computer, if it is switched off. It is a quick deterrent for a less ambitious intruder. The security is far from foolproof as there are several ways to bypass the BIOS password. Almost all of them include physically opening your computer. When you have done this, you can reset the BIOS or simply take out the hard drive and put it into a different computer that does not have BIOS password protection. Hence, if you have a lock on your well-built and strong computer case, you are again increasing the security of access to your information. If you forget your BIOS password, you will have to resort to the methods described above to reset it.
SOFTWARE INSTALLATIONMost computers come pre-installed with software.. Bear in mind that this may be detrimental to your computer's security. All you really need is your Windows CD and the Security-in-a-Box toolkit to get started. You can find all other necessary software on the Internet and all of it free15. Software pre-installed on a new computer often has many trial versions of virus cleaners, graphics packages and what nots. It may also contain spyware (the Chinese government is considering a law that requires all manufacturers and retailers to pre-install censorship software on all new computers). If you stick to using recommended and trusted software tools, install a fully functional virus cleaner and a firewall, you will be a lot more secure when connecting to the Internet for the first time.When installing new software, investigate the publishers in advance and make a decision about their trustworthiness.Do not install unnecessary software that may decorate your computer monitor or make filling in Internet forms easier. It is usually this very software that carries many of the bugs described in this Manual. Do not think that a computer can handle every piece of software you choose to install. If all you need a computer for is checking email and writing documents, all you will require are OpenOffice (http://openoffice.org) and Mozilla Thunderbird (http://mozillamessaging.com/thunderbird/). Don't install anything else. It's that simple.
13 14
15
|