|
Digital Security and Privacy for Human Rights Defenders |
2.6 Circumvention of Internet censorship and filtering
Abstract
This chapter will show you different methods of bypassing Internet censorship and protecting yourself from keyword filtering. In other words, it will explain how to access blocked websites, how to conceal from surveillance mechanisms whatever you are reading or sending on the Internet, and how to hide your movements on the Internet. For non-technical readers, it is advisable to first review the previous chapter on 'Internet surveillance and monitoring' as well as the 'Internet explained' appendices, in order to understand this section in full. Censorship RevisitedInternet censorship is possible due to the very building blocks of networking and the world wide web. Many nations that ban access to websites from their populace do so by installing 'blacklists' on the entry/exit point of the network – the gateway. These lists contain the names of sites (their URL) and often the IP address of the webserver they are hosted on. Requests for blacklisted sites are processed by the gateway and rejected. The event itself is logged and may later lead to retribution. Proxying The ConnectionBlacklists are effective only when a website is requested directly. If a third party is called to fetch a page's content for us, then these lists become irrelevant. For over a decade, netizens living in censored Internet environments have been using online translation and caching services to access a website indirectly. Others have relied on anonymisers, whose original intent was to conceal your identity from a website — to now hide your true destination through the censoring filters.If you are not allowed to access www.bbc.co.uk in your country, you can ask another computer (a proxy) to fetch the website for you. This proxy will be located in a different country that is not restricted by the censorship rules of your Internet environment. To the censor, you will simply be accessing a computer (or website) that is not present in their filtering lists. There are thousands of such proxies, set up in many different ways, and their mission is to be the intermediary between a client's computer and a host website. 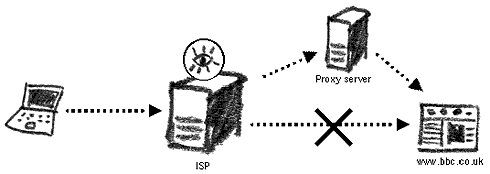
Re-routing a censored connection through a proxy server Proxy services come in different shapes and sizes. It is important to distinguish between their functions and security provided. At all times, bear in mind, that you cannot control the method for communication nor the privacy of the connection between your chosen proxy server and the requested website. This chapter is concerned with methods to reach a functional proxy service and escape the country's censorship mechanisms. AnonymisersThe simplest type of proxy server to use is also known as an anonymiser. The coding for proxy server operations is built into a webpage , through which you can browse the Internet directly. Originally created to hide your true location from the website visited, they also function to conceal your true destination on the Internet. 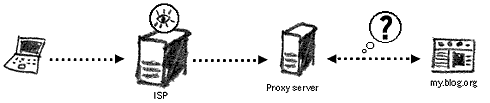
When using anonymisers, the visited website does not know the origin (the real IP address) of your computer. The ISP does nit know your true destination Some of the more well-known anonymisers are:
Their popularity, however, has led many countries that practise Internet filter- ing to block access to these sites as well. Bear in mind that if your Internet connection to the anonymiser is made over an open channel (HTTP as opposed to HTTPS – see the following chapter for more explanation), the data sent and received through this service is not protected from surveillance.
Using Encrypted Proxy ServicesAn encrypted tunnel is created between your computer and the proxy service you have decided to use. Internet surveillance mechanisms do not see the information sent and received through this service, only that you are connecting to it. Using encrypted proxy services adds privacy to your circumvention techniques and is recommended in all instances. Be aware, however, of Man-in-the-Middle attacks (see the following chapter) and know that information you send and receive is not hidden from the proxy service provider itself. 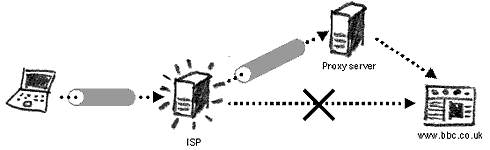
Encrypting your connection over SSL to the proxy server Private CircumventorsThese are proxy servers, set up by your friends or colleagues living infrom the countries that do not filter the websites you wish to access. Its like having your own portal to the unrestricted Internet. The main advantage of these private circumventors is that they use trust networks – a group of friends or colleagues sharing their computer resources to help each other. Such networks provide for greater privacy as they are not known on the public Internet and hence are difficult for the filtering mechanisms to detect and add to their block lists. 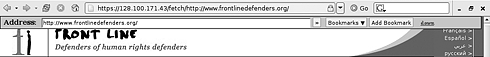
The Psiphon CGI proxy will fetch websites for you that may be blocked in your country For TechiesPeacefire Circumventor55 – allows you to create your own proxy server for others to use. You will need a dedicated computer and a static IP Internet connection to install and run this server. It is recommended that your server is installed in a country that does not implement Internet censorship. The connection details to your computer/proxy server are then passed to users living in the countries that do implement censorship. Virtual Private NetworksAnother way to bypass Internet censorship is with the use of virtual private networks (VPNs). This basically refers an office network extended across the Internet. Many organisations use VPNs when they want staff to have access to network drives and internal resources, whilst not present in the office. VPN's create encrypted connections to the central server and route all information sent and received from the computer through this connection. Hence, if your VPN server is located in a country that does not practice Internet censorship, you may use this service to route Internet traffic through.Your Freedom56 and HotSpot Shield57 are examples of services that let you access their VPN for circumvention purposes. You will be provided with login details and software with which to connect to their servers with. Bear in mind that these methods are useful for disguising your destination on the Internet from mechanisms located in your own country, not from the providers of the service. ANONYMITY NETWORKSAnother approach would be to join one of the anonymity networks that exist on the Internet. Browsing the Internet through such a network would disguise your true identity from any computer or website and will probably make any filtering and data retention in your country innefective. One such network is Tor (http://torproject.org) an abbreviation for The onion router, with an interface in many different languages and a huge team of supporters and contributors around the world. Originally developed by the US Naval Research Laboratory to assist defence and intelligence services in anonymous Internet browsing, it is currently maintained by a worldwide collective of security and anonymity specialists.Tor relies on a large network of servers, provided by volunteers around the world. There are currently around a thousand such servers. When you join this network, your create a random circuit passing through three or more Tor servers, negotiating a separate set of encryption keys for each along the way. This ensures that no single server used to create your circuit can trace your final and original destination. Imagine that you send a letter to a friend and package it in several different envelopes writing a different address on each one. The letter will be sent around and not one of the addressees along the route will know both the origin and final destination of the letter, but only the previous address it came from and the next one it will be going to. Should any of the addressees wish to open the letter, they would not be able to read its content, as it will be encrypted with a password that relies on other two addressees (servers) to decode. When you are using Tor, the ISP or the national surveillance agencies do not know what websites you are looking at and hence cannot prevent you from doing so. The website that receives your query does not know where this query originated. There are over one hundred thousand clients using the Tor network to increase the privacy and anonymity of their Internet browsing. 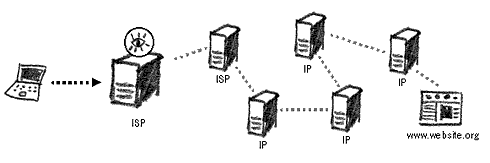
Anonymising your Internet presence on the TOR network You may also use a mobile version of Tor, called Tor Browser. It does not need to be installed on your computer and can be carried around on a USB memory stick, useful for Internet cafes and when using other people's computers. It comes pre-configured with its own Internet browser already set to use the anonymity network58.
A Word On Anonymous Internet PublishingThose who maintain (or contribute to) a blog or an Internet forum need to be aware that their anonymity will not be guaranteed merely by signing with a pseudonym. Every blog entry records the IP address of the computer it was sent from, and many ISPs record all traffic that has passed through them. Therefore, if you are publishing sensitive information on a website, you must take precautions not to be found out. By using anonymisers and anonymity networks you can disguise your IP origin from a particular website; by using an SSL proxy you can hide the article you are uploading from the ISP.For an extensive guide to online publishing, see 'Guide for bloggers and cyber- dissidents' from the Reporters sans frontières web page.59 SUMMARYThe tools and techniques, described in this chapter, are useful to those living under the regimes that apply strong censorship and filtering to the Internet. With their help, you can get around some of the blocks to accessing websites and regain some privacy when publishing material online. Bear in mind that the countries practising Internet censorship and filtering are constantly on the lookout for new proxy servers and privacy tools with the intention of blocking access to them as well. In response, users from all over the world are setting up new proxies every day – a true cat and mouse game.
51 52 53 54
55
56
58
59
|
