|
Digital Security and Privacy for Human Rights Defenders |
2.9 Malicious software and Spam
Abstract
Malware is a term used to describe software that damages your computer and compromises your security and the confidentiality of your information. It can be broken up into several categories, including viruses and spyware. Millions of computers around the world have been infected by a virus or spyware, causing huge problems in the industry. The Internet has become the most widely used medium for spreading malware, and we are always battling to protect ourselves from myriads of old and newly written malicious infections. On today's Internet, a computer infected with malware can be used by third parties to orhestrate digital attacks on other systems. A vulnerability in a computer's defence systems is exploited by infecting it with the attacker's particular virus. The virus gives its creator remote control of the computers, creating what is known as a Botnet. These Botnets can then be used to attack a particular website or the servers of an organisation or government. Such attacks are called Distributed Denial of Service (DDoS) attacks as they overwhelm the servers by making millions of simultaneous requests for service. Such attacks have gained widespread popularity during the last decade, and are often implemented by using an array of infected computers. Websites of human rights organisations are frequently disabled by them. It is very difficult to counter a DDoS attack and preventing the initial infection is key. It is too late to be ambivalent about virus protection, since unbeknownst to you, your infected computer could be participating in a DDoS attack against a website. VirusesSimilar to a human virus, computer viruses infect computers and other technical devices with the intent of changing their stability, operation or integrity. They are usually small pieces of software code that are executed on your computer following a specific action you take. They also have a tendency to re-create and multiply. You can receive a virus in an email, on a USB memory card or by simply browsing to a specific website. Sometimes it is possible to be infected by a virus just by being connected to the Internet. HistoryThe first recognised instance of a spreadable computer virus was the Elk Cloner. It was written around 1982 by a 15-year-old high school student Rich Skrenta and was aimed at Apple II systems. Elk Cloner spread by infecting the Apple II's operating system and was transmitted on floppy disks. When the computer was booted from an infected floppy, a copy of the virus would automatically start. Whenever a new floppy disk was inserted into an infected computer, the virus copied itself to it, thereby allowing itself to spread. It did not cause specific harm to the computer, but was merely an annoyance. On every 50th booting, the virus would display a short 'poem':
Elk Cloner: The program with a personality
It will get on all your disks It will infiltrate your chips Yes it’s Cloner! It will stick to you like glue It will modify ram too Send in the Cloner!65 The Morris Worm, written by Robert Tappan Morris in 1998, became the first well-known malware spread on the Internet. It was estimated to have infected around 6,000 computers worldwide and led to the creation of a new industry for countering similar attacks, headed by CERT (Computer Emergency Response Team), a US federal-funded research institute and development cen- tre (http://www.cert.org). The MyDoom virus of 2004 accounted for 1 in 12 of every email sent on the Internet and was able to co-ordinate the biggest Distributed Denial of Service attack65, involving more then 1 million computers from all over the globe. Malware variationsThere are numerous types of malware, and each has a specific method of operation and distribution.
Mobile phones are also affected in today's virus filled world, taking advantage of Bluetooth and Media Messaging to spread themselves around. BlackBerries are not excluded with a vulnerability that allows malware to become trusted applications. Skype and MSN, iMac built-in video cameras and even newly released wireless pacemakers can all be 'owned' by a virus writer. Malicious code has been found in images on photo sharing websites and millions of unsuspecting (and poorly configured or not updated) web platforms have been 'injected' with viral code . Either our ignorance or their creativity has spawned a hostile digital world with little room for error. Your only hope is to arm yourself with good software and a bunch of common sense – to build a castle for your digital home. You need to:
In 1999, BubbleBoy becomes the first ever worm that did not depend on the user opening an email attachment to be infected. As soon as the infected email message is viewed, the worm is set to work. This trend is followed by many virus writers and continues to baffle the most expensive security systems whilst preying on our never ending curiosity to see the content of a suspicious looking email. 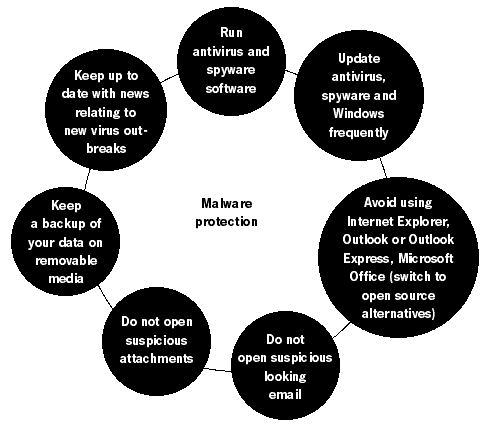
You are defenceless on the Internet if you do not have an anti-virus, anti-spy- ware and firewall software installed. These need to be constantly updated and rigorously configured. You shouldn't have to spend any money at all. Companies like Avast, Comodo and Safer Networking offer free home use of their anti-malware and firewall software.66 SpamSpam is the process of sending bulk and unsolicited emails. They normally take the form of advertising or nonsense messages that often fill up our email boxes. Spam is an activity aimed at increasing the profits of companies, and increasingly of spam gangs. It is a lucrative method, for the costs of mass distribution are minimal – far cheaper then postal junk mail and other means of mass advertising. Spam now accounts for 50% of all Internet activity and is an enormous problem to individuals and to businesses. This section will tell you how to reduce the amount of spam in your email box. HistoryThe concept of spamming as an advertising technique was first introduced in 1994 by two New York immigration lawyers wishing to promote their servic- es through mass emailing. They argued it was a viable and justified new method of marketing and labelled their critics as "anti-commercial radicals". Since then, the popularity of 'spamming' grew very quickly.Preventing spamThere are several methods of reducing the amount of spam you receive, although you may never be able to get rid of it completely. If you are using a webmail account (like Hotmail, Gmail or Yahoo), the provider should have automatic spam filtering software installed.The main method of spam prevention is not to reply or to click on any links in the spam message. Even if you are upset by the amount of spam and wish to reply to the message with a complaint or a request to stop the spamming, you are simply confirming the existence of your email address and labelling yourself as someone who reads spam and reacts to it. Never purchase anything advertised in spam messages. Even if it is legitimate, you'll end up further funding the spammer market. Do not list your email address on any websites or list servers. If this is not possible, disguise it by putting # or 'at' instead of using the normal @ symbol. This will prevent web-spiders from capturing your email addressing If you are sending a large group email, insert the contacts into the 'Bcc' field. This will hide the existence of the mass email and prevent spammers from using the list for their purposes. Try to use several email addresses. One will be your private email which you will give out only to trusted contacts. You can use other addresses for registration and authentication when on the Internet. Thus you will be able to separate private email accounts from those that get spammed. If your account is already facing massive spamming and the filters are simply not working any more, you have no other option but open a new email account and be more vigilant. 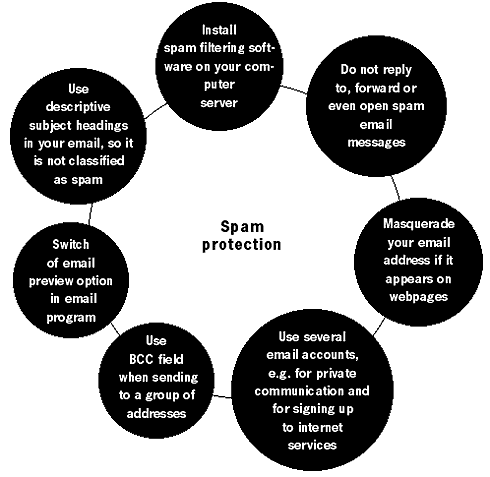
64
65
66
67
|
