|
|
2.10 Identity Theft and Profiling
Abstract
- Your digital identity is a collection of computer, telephone and Internet records that either relate to you or could be used to identify you. It also comprises information you (as well as friends and colleagues) share on social networking sites and blogging platforms.
- Profiling makes certain assumptions about your habits, character, political or social affiliations, as well as those of your friends and colleagues. The Internet is an excellent resource for those wishing to profile your identity.
- Anonymity is an important tool for activists working online and using communication technologies, however it is a difficult task in the midst of modern day technology.
This chapter deals with your digital identity and describes how modern technology is being used to profile your persona, activities and associations with others. It touches upon some topics already covered in this manual including surveillance and anonymity, and attempts to reveal the inherent pitfalls and insecurities of Internet and mobile technology. Its purpose is to inform the reader of potential vulnerabilities for privacy and freedom of association existent in today's Internet and telecommunication infrastructure and to provide advice on how to manage and reduce their impact
Whilst many are accustomed to terms such as Web 2.0, social networking, twittering, video-casting and the like, not nearly enough attention is afforded to the invasive capabilities of the world-wide network infrastructure that provides these services. The temptation of instant communications and access to information offered by modern technology must be balanced with the inherent pervasiveness of these tools to reach into our private lives and collect records of our activities and networks of friends.
Network intelligence capability exists well beyond highly developed and tech- nology friendly countries. The trend common place in the global arms trade – countries willing to sell outdated technology to any buyer who can afford it – applies to surveillance and security technology as well. The centralisation of public and private databases, often pushed through legislative and financial barriers in the name of national and global security, as well as the popular adoption of communication devices and services by us all, works to reduce and often eliminate the privacy and anonymity of our identity – a right inherent and enshrined in numerous international covenants and frameworks.
A Digital Identity
In the physical world we are identified by passport to our government and by recognition to our friends. Further documents and information such as a drivers licence, a social security or tax file number and our reputation serve as distinguishing features of our identity and associations.
Modern technology is a lot more pervasive and thorough than the world we were used to. Numerous identifiers of our personal life, habits, movements and social affiliations are collected and stored. Analysis of this data and assumptions made as to our private and professional lives is called profiling and covered further on in this chapter.
Our digital identities can be collated from several pieces of information, usually created and advertised through our own actions, or those of our friends and colleagues. Whenever using the Internet you are identified by the IP address currently assigned to your computer (see Chapter 2.5 and Appendix B). In the case of working from home or your workplace, this IP address can be quickly associated to your real identity – you had registered and purchased Internet access from a local provider who knows your name and address.
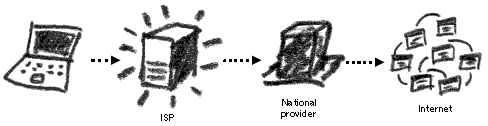
You can be identified on the Internet by many distinguishing factors
A similar principle is valid for mobile telephone communications. Had you registered the phone number in your name, all calls made or received at this number are associated with you. Additionally, every mobile telephone's location can be identified through a process called triangulation – when several of the telecommunication towers in range of your handset can calculate where you are, precise to within a few metres. It gets even trickier. Every phone handset is identified by a unique IMEI number (...). This number is also recorded for all communications made with that phone. Changing the SIM card in a phone previously tied to your identity (through the IMEI) may not provide a great deal of anonymity.
3rd generation mobile phones – those that provide Internet access and GPS (Global Positioning System) coordinates reveal your exact location and very often your identity to the service provider. It is known that the handset can reveal its coordinates when the device is powered down. Mobile phones continue communicating with the telecommunications towers by sending a brief signal of activity when they are switched off68. Due to this reality, mobile telephones can be switched on remotely by the provider. One of the identified solutions is to remove the battery of the device altogether, thereby disabling its capacity to power any of its functions.
An email account and address may be positively linked to your real identity as well. This is obvious for accounts registered under a real name, and is also possible for anonymous accounts that are accessed from a location where the IP address is associated with you.
The same principle applies to your blogging and Internet chat accounts, social networking logins, forum registrations and Internet game profiles. As previously discussed in this manual, a record of communications is collected by your Internet and mobile service providers. With enough information about your digital traffic, a positive identification between your digital communications device and real identity is possible.
Computers infected by malware may expose confidential details of the user, revealing information about their activities to a third-party. For more information on dealing with these threats, please refer to Chapter 2.9.
Digital Profiling
When a digital identity is positively (or mistakenly) linked to a particular individual, profiling becomes an invasive concern to privacy. A history of Internet browsing and email communications can reveal important information a person, their habits and associations with groups and other individuals. Assumptions can be made as to their political and social viewpoints, allegiance and, most importantly, future actions.
Profiling is a term generally applied to collecting and finding patterns in behaviour or within information on people already stored in various databases, in order to determine or predict a particular trait or action, of person or group. It may be used by marketing and financial institutions to analyse consumer preference and interaction with a product or service. It is a prevalently common method to thwart criminal intention, attempting to predict and identify the perpetrators before they are able to commit a crime. Widespread in the air travel industry, profiling was introduced to prevent potential criminals and terrorists from boarding the plane in the first place.
Apart from collecting criminal records, credit ratings, employment and medical data, modern day profiling includes collected digital identities – to increase its effectiveness and reach. Records of mail sent and received, telephone calls and website visits are stored and may be analysed for trends, patterns of behaviour and association. A common example is the Google Email and Applications platform – that provides free services to millions of subscribers, funding its service through content based advertising. Software built into the Google infrastructure scan email and communications to provide 'relevant' advertising on screen. Customers agree to this policy when creating their accounts.69 How Google will react when this information (i.e. what we store and communicate using Google's technology) may be required by the US government is difficult to predict, but the possibility is enough to imagine the pervasiveness and possibility for profiling today. Similarly, it is even harder to predict how the corporation will act and comply with foreign governments. For example, in China, Google was willing to install filtering rules to censor the results of searches made by Chinese citizens, to comply with local legislation. Several times a year, leading technology companies and governments meet to discuss progress and new developments on Internet and telecommunications surveillance70.
It is not only a person's actions that may reveal (or distort) information on their
identity, but also what others are saying to or about him. An email destined for his mailbox makes a statement on his profile (on today's Internet) by its content, whether received or not as yet. Email sent to a group of addresses automatically binds and creates associations between these people, whether true or desired by each individual recipient. Our profile is susceptible to, and often affected by friends and colleagues communicating with us.
Few examples come close to displaying the potential of profiling as much as social networking services. Members of the public willingly upload a huge amount of personal information onto the Internet, create associations between friends and colleagues, reveal their location, photographs and contact details, with an ever increasing pressure and lure to join this 'media revolution'. Marketers, governments and digital adversaries have never had it so easy. The Iranian Revolutionary Guard spent a lot of time on the Twitter platform watching as demonstrations and actions were being planned, sometimes posing as activists and thwarting these activities before they even happened.71 Twitter may have helped them identify (or confirm) the identities of protesters and social activists.
Once recorded, information is very tough to delete (see Chapter 2.3 for more detail) and this also applies to social networking tools. A personal Facebook page will be scrutinised by professional affiliates – even if it has no relation to the job at hand. Government sponsored media, wishing to ridicule or find 'dirt' on members of a human rights NGO may investigate not only the existence of social network pages for any of the staff, but also those pages of their friends, and friends of friends. Once a bad apple is found in the midst of these worldwide contacts, a story may be spun to affect reputation and credibility.
Profiling is not something one can escape in today's technical infrastructure. However, awareness and caution may help people limit or even define information that is collected and collated about them. The integration of technology into one's professional and personal life now means more exposure to profiling and an additional vulnerability to the privacy of users.
Authenticity and Authentication
The global and impersonal nature of the Internet means that new methods are required to authenticate information and people. Till now, the user has identified himself to his email account with a username and password. The account is linked to their identity and the associated name is to display to the authenticate messages sent to friends and colleagues. A username is used by participants of Internet chat sessions, forum contributors and owners of social networking pages.
As previously discussed throughout this manual, much of the content that trav- els the Internet is liable to surveillance. On top of this, a lot of the identifiers we use to authenticate people in the cyberspace can be faked. An experienced adversary can easily spoof their email address to match yours (see Chapter 2.5) and send messages on your behalf. By digging deeper into the coding of the message one can uncover the real identity of the sender, but not nearly enough of us have been shown how to do so (see Appendix B – Email).
The authenticity of an email cannot be trusted if it is impossible to verify the true sender. Amnesty International, for example, recognises this problem, and all its email communications carry a disclaimer at the bottom:
"..Internet communications are not secure and therefore Amnesty International Ltd does not accept legal responsibility for the contents of this message. If you are not the intended recipient you must not disclose or rely on the information in this e-mail.."
When chatting (on MSN or Skype) you assume that the conversing party is the person who they claim to be, albeit without the advantage of vocal or visual recognition to confirm this. A compromised or spoofed account can create a dangerous vulnerability for the privacy and security of people who communicate with this chat account relying on its credibility.
It is quite difficult to determine the interlocutor's true identity in an Internet chat using digital methods. One must resort to the old, well tried means of identification – revealing pre-arranged or personal details, known only to the conversing parties. This can be a secret word or question shared upon initiating a chat. Associate the account or username to the actual person that you know.
Real time identification is slightly more problematic in email. The sender may not have included any details authenticating their identity (bar the email address). Likewise, the threat of email interception and the modification of content remains a real and constant possibility.
Digital signatures were created as an answer to the uncertainty of Internet- based authentication. They employ encryption to record the contents of your message and your identity, secured by a strong pass phrase. If the message is tampered with, the digital signature will become corrupt and the receiver will be made aware of the message's invalidity. When you have implemented a good system of public key encryption, your digital signatures will be of utmost value in authenticating your message to the recipient, or his/her message to you. See Chapter 4 on Cryptology for more details on digital signatures as a method of authentication.
Towards Digital Anonymity
True anonymity is a difficult feat in the modern world of communications technology. Too many activists have already been exposed and punished for publishing articles under pseudonyms, sending text messages and making phonecalls to each other. They may not reveal any details to identify each other in the content of their messages, but inadvertently use technology that has these features built in.
The solution is to be aware of how a particular device, message or action online be associated with your true identity and take necessary steps. Some degree of anonymity can be achieved by registering an obscure email address with a random account name. It is best done from a public computer (for example, in an Internet café or a library) where the IP address cannot be associated with you. Choose a widely known service, like Hotmail or Gmail and an email address that does not include a name or other traceable keywords. Do not include these details anywhere in the message and try to be careful when revealing the address to others.
When browsing websites, pay attention to how activity can be monitored. If you wish for relative anonymity when browsing to undesired websites (however those may be defined in the country), do so from public computers. Anonymity networks like Tor or anonymous proxy servers (see Chapter 2.6 for more details) can be used to disguise true destination and origin of your queries. Try not to lax on this approach by browsing to an 'undesired' website from your personal Internet connection 'just this once'. Once a track record is created, it will probably remain on the provider's servers for a long time.
When using mobile phones, new devices and SIM cards possess some degree of anonymity. Pre-paid SIM cards and unregistered mobile handsets may anonymise the identity of the conversing parties. Expect the degree of anonymity to decrease with each usage and switch to using new devices regularly. In some countries, it is also possible to purchase SIM cards and phones with unregistered (or corrupted) identification tags, but this may not be legal in all jurisdictions.
It is probably too late to anonymise your existing digital identity, whether on the Internet or mobile telecommunications. Create new accounts and mobile telephones numbers in the pursuit of an anonymous communications medium. Pay attention to the place and method of registration, correspondence made through this service or device and its association with others.
Be vigilant, aware and careful of your actions on the Internet and the mobile network, if anonymity is integral to your security.
|

