|
Digital Security and Privacy for Human Rights Defenders |
2.4 Cryptology
Abstract
HistoryCryptology is concerned with linguistic and mathematical techniques for securing information. The messages are coded to become unreadable to everyone but the intended recipient. Its long and colourful history goes back to around 5th century BC when the Spartans created the earliest known method of encryption using two identical wooden staffs and a piece of parchment. The parchment would be wrapped around the stick and the message written lengthwise. Unwrapped, the letters did not appear in any comprehensible order. The parchment was sent to the recipient, who had an identical staff to read the message on. Other methods to secure information from outsiders include lin- guistic cryptology (e.g. hieroglyphics) and steganography, which is the process of hiding the existence of the message itself. The message written on the parchment along the length of the stick (scytale). The scytale uses what is now known as a transpositional cipher, whereby you The security, provided by cryptography alone, should not be overestimated. Its fallibility is usually a result of human error or a bug in the overall security procedure. The use of cryptography has also been restricted by legislation in some countries. Mathematicians, scientists and civil rights activists in the US waged a 20 year battle to prevent the government prohibiting public access and use of cryptology, in what is now known as the Crypto Wars. 
EncryptionEncryption (and its opposite – decryption) is a popular study in the field of cryptology. Encryption works by applying a large mathematical pattern to a set of data and coding it so that it appears incomprehensible to anyone who does not have the decryption method, otherwise known as the key.Disk encryption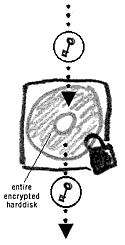
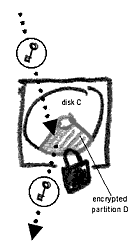
You can use encryption to protect your entire hard drive. You will in essence encrypt every bit of information on it, so that only you, having entered a password, can access this data. Whenever data is extracted from your computer (for example, an email attachment) it is automatically decrypted. If your computer isstolen, the information on it will remain inaccessible to others29. You can also create an encrypted virtual drive on your computer. This option may suit those who do not wish to encrypt their entire computer, but allocate a space where to store information securely. If your computer has 5GB of free space, you can create an encrypted container and allocate 1GB of space to it. It will appear as a new drive on your computer (in fact this drive is not new and hence referred to as virtual). n will be encrypted, and you can store your documents on it. partitioThis You can set your email program (e.g. Thunderbird) to store all files on the encrypted partition. Only you, or the bearer of your password, will be able to access the email on this partition. You can also encrypt anentire USB memory card or other removable devices. This is useful when travelling with all of your documents on the memory card. Software like True Crypt, can also be run directly from your USB card, so that you will not need the program installed on every computer you wish to access your encrypted documents on.
Public Key EncryptionTraditional methods of encrypting the information you wanted to share with another person required you to give them the password to decrypt it. This was not a very secure method, as it was possible to compromise your password in the process. To get around this problem, mathematicians developed public key encryption (PKE). It is the most common method of encrypting communications (e.g. email) today.When using PKE, your key will be made up of two parts: a public and a private key. Together they will make up your key pair. The keys are intertwined and what you encrypt with one, you can decrypt with the other. This is an integral part of PKE and a basis for its security and fallibility. You share your public key with anyone you want to communicate with. You can also upload your public key to a key server on the Internet. The private key is kept secret on your computer or floppy disk and additionally protected with a password that only you should know. Do not share your private key with anyone. If you think that your password has become compromised (stolen) then you will need to revoke your key pair and recreate them from scratch. Encrypting and decrypting a message30In the PKE system, messages are encrypted for sending to us using our public key, and we decrypt them using our private key. People obtain your public key when they wish to send you an encrypted message by asking you for it or finding one you left previously on an Internet key server.Example: You have a message that you wish to send to me encrypted. First, I must give you a copy of my public key. You use this public key to encrypt the message and send it back by email or other means. Only I will be able to decrypt this message since only I have the missing link – my private key. 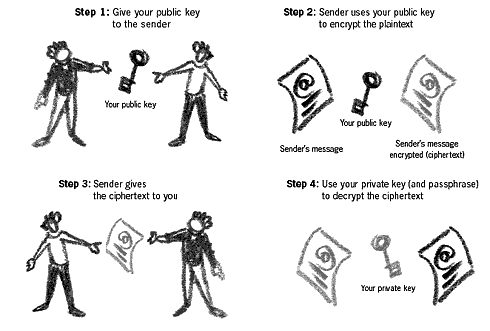
Note: by “plaintext” we refer to the original message and “cipher text” refers to the message once it has been encrypted. This facilitates communication of encrypted messages without having to share a password and dramatically increases the security and practicality of your communications. PKE has been applied to email, Internet chat, web browsing and many other Internet services. Its security has caused controversy with many governments. The level of privacy offered by the successful application of this system has made many surveillance and intelligence agencies very worried. Key SecurityThe reliability of the encryption depends on :
The PKE infrastructure relies on the valid identity of the public and private key. When you are encrypting a message to me using my public key, you want to be sure that this key belongs to me. Let's have a look at the properties of a key pair. A key pair is identified by 5 distinct features:
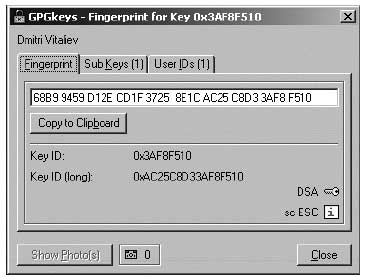
Fingerprint as seen in the GPGshell program Try and verify the above details before using someone's public key to communicate with them. Since public key encryption does not require you to share a password with the message recipient, it is important that you can validate the true identity of the public key. Public keys are easy to create but the identifying features can also be falsified. That is why you should authenticate the person's public key before you use it (see 'Digital signa- tures' below). Once you have established that the public key belongs to them, you can 'sign' it. This will tell the program that you trust the key's vali- dity and wish to use it.31 The key size is usually 2048 bits. This level of encryption is assumed to be far more complex than modern computers can break32.Digital Signatures - For TechiesWe need the ability to verify the authenticity of our messages. This can be done by a digital signature, which also uses PKE to function. When you digitally sign a message, you include in it a unique mathematical calculation derived from its size, date and specific content. This digest is then encrypted with your private key so that the recipient can verify its validity. Once decrypted, the original digest in the signature is checked against the file received and confirms whether the file has been modified or not since it was signed. It is virtually impossible to change the content of your message without invalidating the signature. 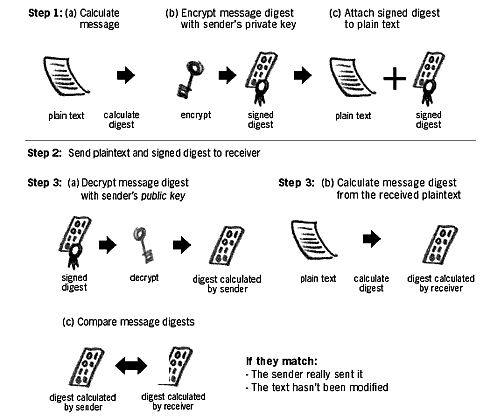
To sum it all up, using encryption is really not so difficult with modern software at hand. The main points to remember:
Encryption InsecurityThe biggest problem with using encryption is that it sometimes gives the user a false sense of security. Just because you are using encryption does not mean that your messages will remain 100% secure. It is, of course, an excellent method of raising your level of security, but it is not foolproof. The main problem with PKE security is the human factor: mistakes that we make by carelessness or ignorance. I will discuss three methods of breaking your encryption privacy.
Choose encryption programs that have been publicly verified to have no back doors (such as PGP, GnuPG, TrueCrypt). Be aware of your local legis- lation and whether it allows you to use encryption and if yes, at what level of complexity (key size)35. You should also understand that the current legislation in your country may oblige you to reveal your password to the authorities. Try to find out if there are any legislative privacy safeguards which you can use to prevent this from happening.
29
30Suggested software with which you could perform PKE is GPG4Win http://www.gpg4win.org or by installing the GnuPG and GPGshell software from the NGO in a Box
31 32 See this article http://www.keylength.com/en/3/ for a description of current and future key length necessities
33
34 35 |
