|
|
3.2 Case Study 2
Communication channels
Outline
The global NGO 'Human Rights for All' (HQ) based in
Europe has requested that one of its international
branches (the Bureau) performs an investigation into cases
of torture at the hands of the local government. The
selected country 'N' has long become notorious for using
torture against prisoners and especially human rights
defenders. The Bureau is located in the capital of 'N' and
employs a number of skilled people with many years
experience of working in difficult situations. They can
collate the necessary information for the report on
torture but worry that the government will stop at nothing
to prevent them from doing so. 'N' has a very tight policy
on controlling information and making sure that the
outside world knows as little as possible about its
internal activities.
HQ decides to publish the report, based on the information
they will receive from the Bureau, themselves. They need
to establish a secure channel of communication with the
Bureau and make sure that the project continues until
completion, or for as long as possible. There is an
understanding that security is a primary issue here and
they have allocated a budget of 5,000 USD to the Bureau
especially for this cause. The project needs to survive
attempts by the local forces to compromise, restrict or
destroy it completely. The Bureau is to undergo a review
of its methods of collecting and communicating information
as well as of building a security policy for all staff to
implement.
It is decided that all staff undergo information security
training by a local expert and do their own study and
research in security issues on the Internet. Case studies,
witness reports and other information on torture cases
they may uncover will be stored on paper and in electronic
format. Field reporters will communicate their findings by
bringing back a collection of notes taken during the
mission, and by making daily reports from an Internet
café. In other words, all information will be duplicate in
physical and electronic format.
The office comprises a rented apartment in the centre of
the city. There are two computers and an Internet
connection. The staff are well-acquainted with the
neighbours and enjoy their support. The office had
previously been broken into, although nothing of
importance was taken.
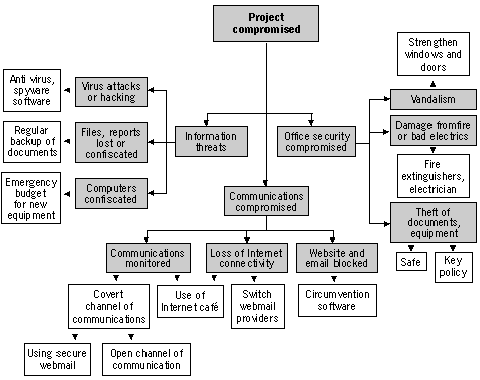
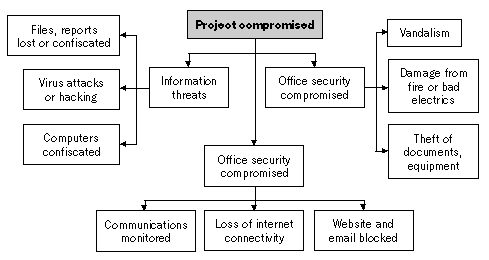
Threats
To get an understanding of what elements the Bureau will
need to secure this project, they first decide to list all
the threats they may face. The project work area is shared
by HQ, the Bureau's office and the field workers. Each face
their own particular threats and these must be dealt with
sepa- rately. Likewise, the threats themselves are separated
into those affecting office, information and communications
security.105
HQ
Office threats: minimal
Information threats: Reports could be lost due to
virus damage or hacking
Communication threats: The communications link with
the Bureau could be broken, or reports could be spoofed
(falsified by malicious intrusions).
The Bureau
Office threats: Vandalism to equipment, theft,
electricity faults, fire
Information threats: Computers are confiscated, data
is corrupted by virus attacks or hackers
Communication threats: Office internet is
disconnected, email does not send or arrive, HQ website and
email address blocked, communications monitored
Field workers
Information threats: reports are lost or confiscated
Communication threats: field workers cannot access
Internet café, the Bureau’s or HQ’s website become blocked
from access within N.
Solutions
Communication
Communication between the different players in this project
is essential to its survival. Therefore the participants
devise several standards and methods of establishing and
continuing this communication.
Three distinct channels of communicating with HQ are
established. There is an open channel, where
information is communicated in an insecure fashion – by
telephone, post and regular email. It is important to have
an open channel, so that the monitoring bodies can be
satisfied of having ready access to the project
communications. Information passed through the open
channel is not sensitive and would include typical
administrative and organisational data.
A private channel will provide for sensitive and secure
communications. It will be used for exchanging information
about cases, witness reports and organisational strategy.
It is decided to use a secure webmail solution and Pidgin
with the OTR plug-in for instant messaging106.
No sensitive information will be passed by telephone, fax
or insecure email. The private channel will not be used
regularly so as not to attract too much attention.
The above channels require a functioning Internet
connection for communica- tion. It is agreed that HQ will
not suffer from Internet shortages and a back- up channel
is devised for the Bureau and their field workers, in case
the Internet stops working or is disconnected. The backup
channel will involve the Bureau workers using a nearby
Internet café. They will use portable versions of the
necessary software, as obtained from the Digital Security
Toolkit and carry it with them on USB memory sticks. They
have received assurance from the Internet café owner, that
the computers are free of viruses. In any case, staff will
use public computers with caution.
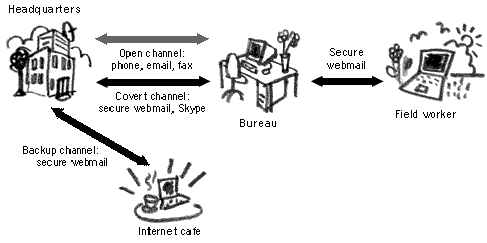
A graphical schematic for the Bureau’s communications
system
Information
All data recorded and collected by the staff will be kept on
paper and electronically. This will require necessary safety
measures to ensure that the data is not lost, stolen or
damaged. It will be very important to create and maintain a
backup procedure that will outlive possible attacks.
Likewise, the backup medium itself will need to be secure,
as it creates an additional copy of sensitive documents.
To make sure that no field reports are lost before they are
transmitted back to Bureau, a laptop will be purchased.
Field workers will record information on paper and duplicate
it to laptop. They will communicate this information to the
Bureau from an Internet café on a daily basis (or as often
as possible).
Office
Office security will include a rigorous policy for the
staff, strengthening of entry points to the building and
general upkeep to make sure that the chances for computer
crashes are reduced. Physical documents will need to be
kept in a safe, and wasted paper will need to be properly
destroyed. It must be taken into account that computers
and other office equipment could be damaged or
confiscated, so a reserve fund is maintained to allow the
organisation to purchase new equipment and resume work
should this occur.
Detailed responses to threats
After developing a general idea of how to operate when
dealing with possible disruptions to their work, the staff
attempt to counteract all of the individual threats listed
in the diagram. They undergo security training and perform
their own research into electronic security on the Internet.
Information threats
Files, reports lost or confiscated: To prevent
the loss of data, regular backup is made of the
information on computers and laptops. A re- writeable CD
drive (CD-RW) is sourced for 200USD and installed on one
of the computers. Information backup is implemented by
using the Cobian backup software available on the Digital
Security Toolkit and files are written to CD with the
DeepBurner107 program. Every second day a backup is made
of all the user documents, put on a CD and taken off-site.
The person to maintain this backup rotates 2 CDs, one of
which is always in the office and the other – at his/her
house. At the end of every month, an additional backup is
made and given to another person to keep at home. This
way, should the computers in the office be damaged and the
daily backup system be compromised (quite difficult to
orchestrate), there will be a third tier of information
backup from the previous month. Backup for field workers
is done on a USB memory stick. The stick contains a copy
of all recent documents, made by reporters since they last
visited the office. If the laptop is lost or confiscated,
the documents can at least make it back to the office.
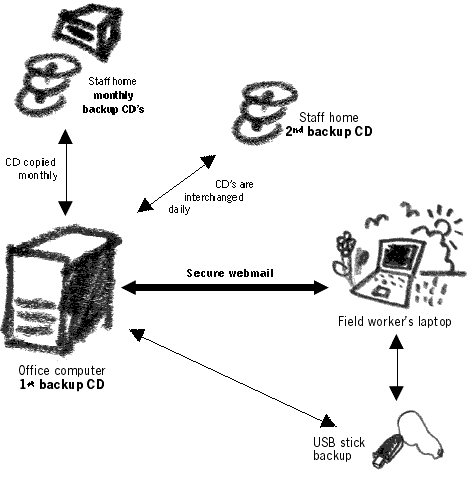
Multiple layers of data backupconfiscated, the documents
can at least make it back to the office
- Virus attacks or hacking: To prevent the loss
of data through a virus attack or hacking, the Bureau
installs the Avast4 anti-virus software on all computers
and laptops. The software is free for non-profit
organisations and updates automatically when the
computer is connected to the Internet. They also install
Spybot to counteract other malicious software and the
Comodo firewall to prevent hackers from intruding into
their computers. All software and explanations are found
on the Digital Security Toolkit. A strong
policy on viruses is introduced, ensuring that nobody
opens suspicious-looking email messages or uses an
external diskette in a computer without scanning it with
the anti-virus software first.
- Computers confiscation: If the computers are
confiscated with official warrants or otherwise, the
organisation must have the means to continue its
operation. It will be necessary to purchase new
computers, and money must be allowed in the budget for
this. Even one computer will suffice if
the circumstances demand it. The staff source a computer
retailer who will sell a new computer for 1000 USD.
Needless to say, a backup of the files and documents
will be required to bring the organisation back to its
original state and allow the project to continue.
- Theft of documents, equipment: A strict key
policy is introduced and only those in need of
possessing office keys are given a copy. No additional
copies can be made without general consensus. All
computers are switched off at night and a safe for files
is purchased at 300 USD. All CDs, diskettes and paper
with sensitive information on it is kept in the safe.
Measures are implemented to make sure that no unwanted
persons could sneak into the office. The windows are
within ground level and will be protected with metal
bars. The door is also strengthened and a peep hole
installed. A local company agrees to do both services
for 500 USD.
- Loss of Internet connectivity: It is possible
that the Internet is disabled from use for the Bureau.
This could be the result of pressure on the Internet
Service Provider or a malfunction of the network
itself. To counteract, the staff decide to use an
Internet café. Should the interruption to the office
Internet connection prove long-term, 500 USD is set
aside as emergency fund to for using the Internet café.
A USB memory card will be used to transmit files between
the office and the Internet café.
- Communications
monitored: If the surveillance infrastructure of N
is sufficiently
advanced, they will be monitoring email that comes in
and out of the
country. The Bureau has a suspicion that their email is
sensitive enough
to warrant its monitoring and switch over to using a
secure SSL webmail
service. They register two accounts at
https://www.riseup.net103
and use one for communicating with
HQ and one for the field workers. All information is
passed to the
headquarters daily via email. Since the connection to
the webmail client
is over SSL (HTTPs), it is encrypted. The Bureau staff
research the
possibility of Man-in-the-Middle attacks and are careful
checking the
certificates presented by the website.
- Website and email
blocked: If the government decides to block
Internet access to the HQ website and to the RiseUP
webmail, an alternative must be found. The Bureau
employees can find other secure webmail providers or
employ a number of circumvention methods to bypass these
blocks. It is decided to ask headquarters to install the
Psiphon tool on their PCs at home. Relevant IP addresses
and login details are passed to the Bureau. These
provides a secure way to circumvent to government's
blocks and provide access to the HQ servers.
- Computer technician: A previously tried and
tested consultant from a
computer company will visit the office twice a month for
general
administration and will be on call for emergency
situations. The fee
will be 1,000 USD for 6 month.
Budget
|
| Bars on windows and door strengthening |
500 USD |
| CD re-writer and 10CDs |
200 USD |
| Safe |
300 USD |
| 2 USB memory cards |
100 USD |
| Laptop |
1,000 USD |
| Computer Technician |
1,000 USD |
|
| Total |
3,100 USD |
|
|
| Emergency money: 1000 for PC, 500 for Internet |
| café, 200 for Circumventing Website blocks |
1,700 USD |
| Budget Total |
4,800 USD |
|